
The advanced persistent threat (APT) actor known as Tonto Team carried out an unsuccessful attack on cybersecurity company Group-IB in June 2022. The Singapore-headquartered firm said that it detected and blocked malicious phishing... Read more »

A previously unknown threat actor has been targeting companies in the U.S. and Germany with bespoke malware designed to steal confidential information. Enterprise security company Proofpoint, which is tracking... Read more »

After the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a decryptor for affected victims to recover from ESXiArgs ransomware attacks, the threat actors have bounced back with an updated... Read more »

Suspected Russian threat actors have been targeting Eastern European users in the crypto industry with fake job opportunities as bait to install information-stealing malware on compromised hosts. The attackers... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added three flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active abuse in the wild. Included among the... Read more »

Four different rogue packages in the Python Package Index (PyPI) have been found to carry out a number of malicious actions, including dropping malware, deleting the netstat utility, and... Read more »
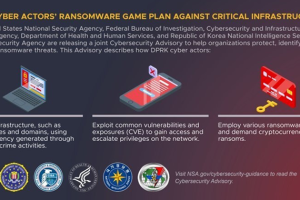
State-backed hackers from North Korea are conducting ransomware attacks against healthcare and critical infrastructure facilities to fund illicit activities, U.S. and South Korean cybersecurity and intelligence agencies warned in... Read more »

Here are three of the worst breaches, attacker tactics and techniques of 2022, and the security controls that can provide effective, enterprise security protection for them. #1: 2 RaaS... Read more »

In a first-of-its-kind coordinated action, the U.K. and U.S. governments on Thursday levied sanctions against seven Russian nationals for their affiliation to the TrickBot, Ryuk, and Conti cybercrime operation.... Read more »

Popular social news aggregation platform Reddit has disclosed that it was the victim of a security incident that enabled unidentified threat actors to gain unauthorized access to internal documents,... Read more »

