
Chinese-speaking individuals in Southeast and East Asia are the targets of a new rogue Google Ads campaign that delivers remote access trojans such as FatalRAT to compromised machines. The... Read more »
Security researchers have disclosed two new vulnerabilities affecting Schneider Electric Modicon programmable logic controllers (PLCs) that could allow for authentication bypass and remote code execution. The flaws, tracked as CVE-2022-45788 (CVSS... Read more »

Telecommunication service providers in the Middle East are being targeted by a previously undocumented threat actor as part of a suspected espionage-related campaign. Cybersecurity firms SentinelOne and QGroup are... Read more »
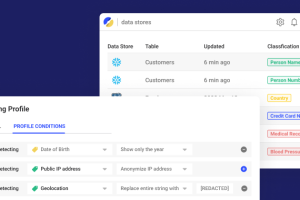
Security teams typically have great visibility over most areas, for example, the corporate network, endpoints, servers, and cloud infrastructure. They use this visibility to enforce the necessary security and... Read more »
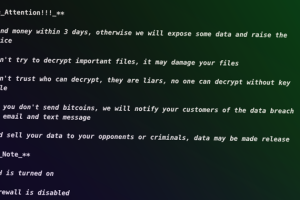
More than 500 hosts have been newly compromised en masse by the ESXiArgs ransomware strain, most of which are located in France, Germany, the Netherlands, the U.K., and Ukraine.... Read more »
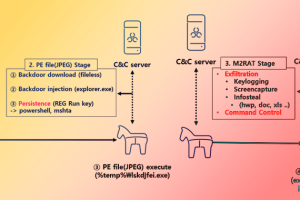
The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group’s features and... Read more »

A new financially motivated campaign that commenced in December 2022 has seen the unidentified threat actor behind it deploying a novel ransomware strain dubbed MortalKombat and a clipper malware... Read more »

Bad actors love to deliver threats in files. Persistent and persuasive messages convince unsuspecting victims to accept and open files from unknown sources, executing the first step in a... Read more »

Cybersecurity researchers have unearthed a new piece of evasive malware dubbed Beep that’s designed to fly under the radar and drop additional payloads onto a compromised host. “It seemed as if... Read more »

In an ideal world, security and development teams would be working together in perfect harmony. But we live in a world of competing priorities, where DevOps and security departments... Read more »

