A sophisticated botnet known as MyloBot has compromised thousands of systems, with most of them located in India, the U.S., Indonesia, and Iran. That’s according to new findings from... Read more »

As the digital age evolves and continues to shape the business landscape, corporate networks have become increasingly complex and distributed. The amount of data a company collects to detect... Read more »

A new information stealer called Stealc that’s being advertised on the dark web could emerge as a worthy competitor to other malware of its ilk. “The threat actor presents Stealc as... Read more »

Popular cryptocurrency exchange platform Coinbase disclosed that it experienced a cybersecurity attack that targeted its employees. The company said its “cyber controls prevented the attacker from gaining direct system access and... Read more »

A spear-phishing campaign targeting Indian government entities aims to deploy an updated version of a backdoor called ReverseRAT. Cybersecurity firm ThreatMon attributed the activity to a threat actor tracked as SideCopy. SideCopy... Read more »

Norwegian police agency Økokrim has announced the seizure of 60 million NOK (about $5.84 million) worth of cryptocurrency stolen by the Lazarus Group in March 2022 following the Axie... Read more »

Russia’s cyber attacks against Ukraine surged by 250% in 2022 when compared to two years ago, Google’s Threat Analysis Group (TAG) and Mandiant disclosed in a new joint report.... Read more »

Unknown malware presents a significant cybersecurity threat and can cause serious damage to organizations and individuals alike. When left undetected, malicious code can gain access to confidential information, corrupt... Read more »
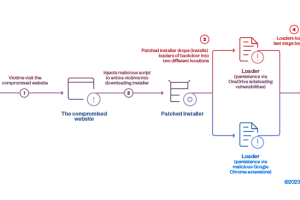
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign. Earth Kitsune, active since at least... Read more »

Samsung has announced a new feature called Message Guard that comes with safeguards to protect users from malware and spyware via what’s referred to as zero-click attacks. The South... Read more »

