
An active malware campaign has set its sights on Facebook and YouTube users by leveraging a new information stealer to hijack the accounts and abuse the systems’ resources to... Read more »

Cybersecurity researchers are warning of “imposter packages” mimicking popular libraries available on the Python Package Index (PyPI) repository. The 41 malicious PyPI packages have been found to pose as... Read more »

Apple has revised the security advisories it released last month to include three new vulnerabilities impacting iOS, iPadOS, and macOS. The first flaw is a race condition in the Crash Reporter component (CVE-2023-23520) that could... Read more »

If you Google “third-party data breaches” you will find many recent reports of data breaches that were either caused by an attack at a third party or sensitive information... Read more »

Shipping companies and medical laboratories in Asia have been the subject of a suspected espionage campaign carried out by a never-before-seen threat actor dubbed Hydrochasma. The activity, which has... Read more »
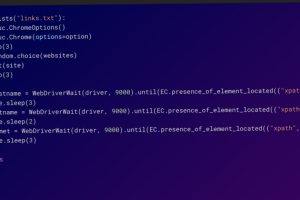
In what’s a continuing assault on the open source ecosystem, over 15,000 spam packages have flooded the npm repository in an attempt to distribute phishing links. “The packages were created using... Read more »

An open source command-and-control (C2) framework known as Havoc is being adopted by threat actors as an alternative to other well-known legitimate toolkits like Cobalt Strike, Sliver, and Brute Ratel. Cybersecurity firm... Read more »

At the beginning of January, Gcore faced an incident involving several L3/L4 DDoS attacks with a peak volume of 650 Gbps. Attackers exploited over 2000 servers belonging to one... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The list of shortcomings... Read more »

VMware on Tuesday released patches to address a critical security vulnerability affecting its Carbon Black App Control product. Tracked as CVE-2023-20858, the shortcoming carries a CVSS score of 9.1 out... Read more »

