
Google said it’s working with ecosystem partners to harden the security of firmware that interacts with Android. While the Android operating system runs on what’s called the application processor... Read more »

Are you prepared to tackle the top SaaS challenges of 2023? With high-profile data breaches affecting major companies like Nissan and Slack, it’s clear that SaaS apps are a... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is urging organizations and individuals to increase their cyber vigilance, as Russia’s military invasion of Ukraine officially enters one year. “CISA assesses... Read more »

The use of AI in cybersecurity is growing rapidly and is having a significant impact on threat detection, incident response, fraud detection, and vulnerability management. According to a report... Read more »
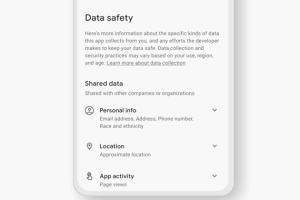
An investigation into data safety labels for Android apps available on the Google Play Store has uncovered “serious loopholes” that allow apps to provide misleading or outright false information.... Read more »
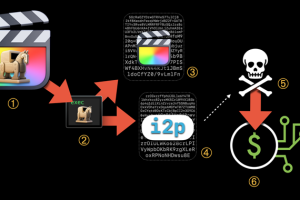
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems. Jamf Threat Labs, which made the discovery, said the XMRig coin miner... Read more »

Multiple threat actors have been observed opportunistically weaponizing a now-patched critical security vulnerability impacting several Zoho ManageEngine products since January 20, 2023. Tracked as CVE-2022-47966 (CVSS score: 9.8), the remote code execution... Read more »
The (Other) Risk in Finance A few years ago, a Washington-based real estate developer received a document link from First American – a financial services company in the real... Read more »
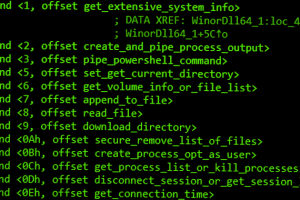
A new backdoor associated with a malware downloader named Wslink has been discovered, with the tool likely used by the notorious North Korea-aligned Lazarus Group, new findings reveal. The payload, dubbed WinorDLL64 by... Read more »

Materials research organizations in Asia have been targeted by a previously unknown threat actor using a distinct set of tools. Symantec, by Broadcom Software, is tracking the cluster under... Read more »

