
As digital transformation takes hold and businesses become increasingly reliant on digital services, it has become more important than ever to secure applications and APIs (Application Programming Interfaces). With... Read more »
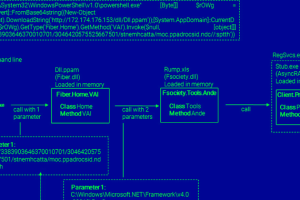
The threat actor known as Blind Eagle has been linked to a new campaign targeting various key industries in Colombia. The activity, which was detected by the BlackBerry Research... Read more »
LastPass, which in December 2022 disclosed a severe data breach that allowed threat actors to access encrypted password vaults, said it happened as a result of the same adversary... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity flaw affecting the ZK Framework to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation. Tracked... Read more »
The RIG exploit kit (EK) touched an all-time high successful exploitation rate of nearly 30% in 2022, new findings reveal. “RIG EK is a financially-motivated program that has been... Read more »

Spoiler Alert: Organizations with 10,000 SaaS users that use M365 and Google Workspace average over 4,371 additional connected apps. SaaS-to-SaaS (third-party) app installations are growing nonstop at organizations around the world.... Read more »

A new ChromeLoader malware campaign has been observed being distributed via virtual hard disk (VHD) files, marking a deviation from the ISO optical disc image format. “These VHD files... Read more »
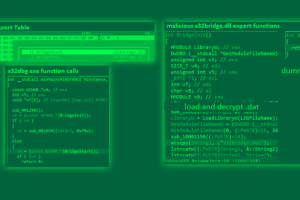
The PlugX remote access trojan has been observed masquerading as an open source Windows debugger tool called x64dbg in an attempt to circumvent security protections and gain control of a target... Read more »

Government entities in Asia-Pacific and North America are being targeted by an unknown threat actor with an off-the-shelf malware downloader known as PureCrypter to deliver an array of information... Read more »

The Dutch police announced the arrest of three individuals in connection with a “large-scale” criminal operation involving data theft, extortion, and money laundering. The suspects include two 21-year-old men... Read more »

