
High-profile government entities in Southeast Asia are the target of a cyber espionage campaign undertaken by a Chinese threat actor known as Sharp Panda since late last year. The... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The list of vulnerabilities is below... Read more »
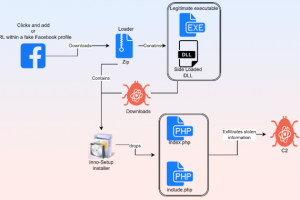
Cybersecurity researchers have discovered a new information stealer dubbed SYS01stealer targeting critical government infrastructure employees, manufacturing companies, and other sectors. “The threat actors behind the campaign are targeting Facebook... Read more »

Investing in digital identity can improve security, increase clinical productivity, and boost healthcare’s bottom line. — by Gus Malezis, CEO of Imprivata Digitalization has created immeasurable opportunities for businesses over the... Read more »

A suspected Pakistan-aligned advanced persistent threat (APT) group known as Transparent Tribe has been linked to an ongoing cyber espionage campaign targeting Indian and Pakistani Android users with a backdoor called CapraRAT.... Read more »

An older version of Shein’s Android application suffered from a bug that periodically captured and transmitted clipboard contents to a remote server. The Microsoft 365 Defender Research Team said it discovered the problem... Read more »

The massive breach at LastPass was the result of one of its engineers failing to update Plex on their home computer, in what’s a sobering reminder of the dangers... Read more »
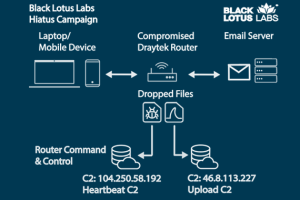
A never-before-seen complex malware is targeting business-grade routers to covertly spy on victims in Latin America, Europe, and North America at least since July 2022. The elusive campaign, dubbed Hiatus by... Read more »

Deep fakes are expected to become a more prominent attack vector. Here’s how to identify them. What are Deep Fakes? A deep fake is the act of maliciously replacing... Read more »

Law enforcement authorities from Germany and Ukraine have targeted suspected core members of a cybercrime group that has been behind large-scale attacks using DoppelPaymer ransomware. The operation, which took... Read more »

