
Google is calling attention to a set of severe security flaws in Samsung’s Exynos chips, some of which could be exploited remotely to completely compromise a phone without requiring... Read more »

The advanced persistent threat known as Winter Vivern has been linked to campaigns targeting government officials in India, Lithuania, Slovakia, and the Vatican since 2021. The activity targeted Polish government agencies,... Read more »
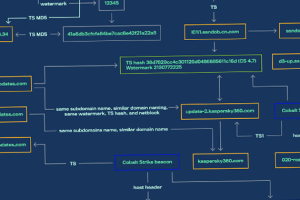
Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that’s designed to load Cobalt Strike onto infected machines.... Read more »

The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems. That’s according to Cado Security, which found the sample after... Read more »

A coalition of law enforcement agencies across Europe and the U.S. announced the takedown of ChipMixer, an unlicensed cryptocurrency mixer that began its operations in August 2017. “The ChipMixer software blocked... Read more »

In last year’s edition of the Security Navigator we noted that the Manufacturing Industry appeared to be totally over-represented in our dataset of Cyber Extortion victims. Neither the number of businesses... Read more »
Multiple threat actors, including a nation-state group, exploited a critical three-year-old security flaw in Progress Telerik to break into an unnamed federal entity in the U.S. The disclosure comes from a joint... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on March 15 added a security vulnerability impacting Adobe ColdFusion to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation.... Read more »
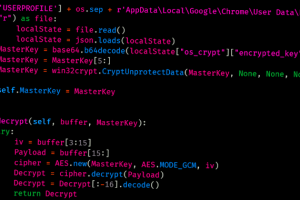
A previously undocumented threat actor dubbed YoroTrooper has been targeting government, energy, and international organizations across Europe as part of a cyber espionage campaign that has been active since at least... Read more »

The stakes could not be higher for cyber defenders. With the vast amounts of sensitive information, intellectual property, and financial data at risk, the consequences of a data breach... Read more »

