
This article has not been generated by ChatGPT. 2022 was the year when inflation hit world economies, except in one corner of the global marketplace – stolen data. Ransomware... Read more »

The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems. Emotet,... Read more »
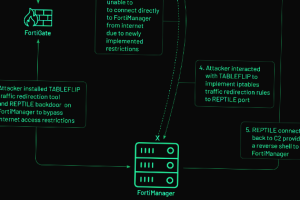
The zero-day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution,... Read more »

U.S. government agencies have released a joint cybersecurity advisory detailing the indicators of compromise (IoCs) and tactics, techniques, and procedures (TTPs) associated with the notorious LockBit 3.0 ransomware. “The LockBit... Read more »

An Android voice phishing (aka vishing) malware campaign known as FakeCalls has reared its head once again to target South Korean users under the guise of over 20 popular... Read more »
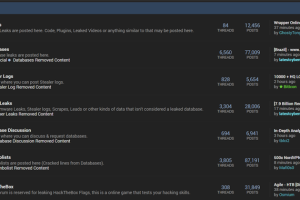
U.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums hacking forum under the online alias “Pompompurin.” The development, first reported by Bloomberg... Read more »
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service (DDoS) attacks. “The malware binaries appear... Read more »

Think of the typical portrayal of a cyberattack. Bad guy pounding furiously on a keyboard, his eyes peeking out from under a dark hoodie. At long last, his efforts... Read more »

In the modern corporate IT environment, which relies on cloud connectivity, global connections and large volumes of data, the browser is now the most important work interface. The browser... Read more »
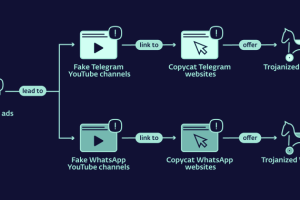
Copycat websites for instant messaging apps like Telegram and WhatApp are being used to distribute trojanized versions and infect Android and Windows users with cryptocurrency clipper malware. “All of... Read more »

