
In a sudden turn of events, Baphomet, the current administrator of BreachForums, said in an update on March 21, 2023, that the hacking forum has been officially taken down... Read more »
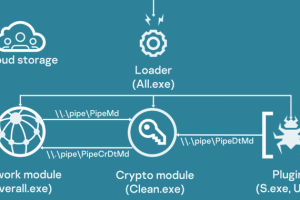
Amid the ongoing war between Russia and Ukraine, government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea have been attacked as part of an active campaign that drops a... Read more »

H0lyGh0st, Magecart, and a slew of state-sponsored hacker groups are diversifying their tactics and shifting their focus to… You. That is, if you’re in charge of cybersecurity for a... Read more »

Poorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different variants of malware called ShellBot. “ShellBot, also known as PerlBot, is a DDoS... Read more »

As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of the flaws discovered in software from Microsoft, Google, and Apple. While this figure... Read more »

Bitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency from hot wallets by exploiting a zero-day security flaw in its software. “The attacker was able to... Read more »
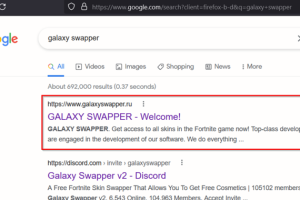
A new piece of malware dubbed dotRunpeX is being used to distribute numerous known malware families such as Agent Tesla, Ave Maria, BitRAT, FormBook, LokiBot, NetWire, Raccoon Stealer, RedLine Stealer, Remcos, Rhadamanthys, and Vidar. “DotRunpeX is a new injector written in .NET... Read more »
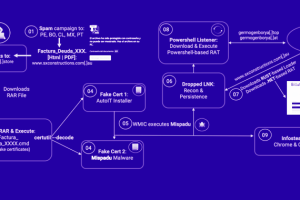
A banking trojan dubbed Mispadu has been linked to multiple spam campaigns targeting countries like Bolivia, Chile, Mexico, Peru, and Portugal with the goal of stealing credentials and delivering other payloads.... Read more »
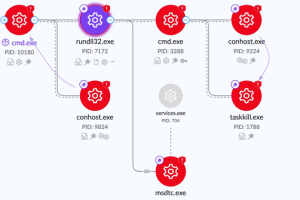
The threat actors behind the CatB ransomware operation have been observed using a technique called DLL search order hijacking to evade detection and launch the payload. CatB, also referred to as... Read more »

This article has not been generated by ChatGPT. 2022 was the year when inflation hit world economies, except in one corner of the global marketplace – stolen data. Ransomware... Read more »

