Microsoft has released an out-of-band update to address a privacy-defeating flaw in its screenshot editing tool for Windows 10 and Windows 11. The issue, dubbed aCropalypse, could enable malicious actors to... Read more »

In what’s a case of setting a thief to catch a thief, the U.K. National Crime Agency (NCA) revealed that it has created a network of fake DDoS-for-hire websites... Read more »
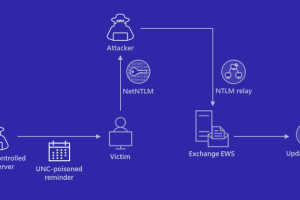
Microsoft on Friday shared guidance to help customers discover indicators of compromise (IoCs) associated with a recently patched Outlook vulnerability. Tracked as CVE-2023-23397 (CVSS score: 9.8), the critical flaw relates to... Read more »

OpenAI on Friday disclosed that a bug in the Redis open source library was responsible for the exposure of other users’ personal information and chat titles in the upstart’s... Read more »

A malicious Python package on the Python Package Index (PyPI) repository has been found to use Unicode as a trick to evade detection and deploy an info-stealing malware. The... Read more »

Any app that can improve business operations is quickly added to the SaaS stack. However, employees don’t realize that this SaaS-to-SaaS connectivity, which typically takes place outside the view... Read more »

Cloud-based repository hosting service GitHub said it took the step of replacing its RSA SSH host key used to secure Git operations “out of an abundance of caution” after... Read more »
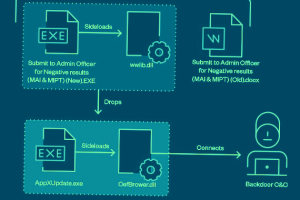
A recent campaign undertaken by Earth Preta indicates that nation-state groups aligned with China are getting increasingly proficient at bypassing security solutions. The threat actor, active since at least 2012, is tracked... Read more »

Patches have been released for a critical security flaw impacting the WooCommerce Payments plugin for WordPress, which is installed on over 500,000 websites. The flaw, if left unresolved, could... Read more »

Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded as OpenAI’s ChatGPT service to harvest Facebook session cookies and hijack... Read more »

