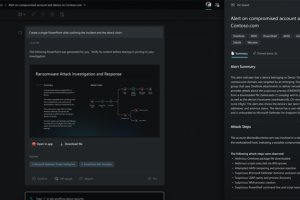
Microsoft on Tuesday unveiled Security Copilot in preview, marking its continued push to embed AI-oriented features in an attempt to offer “end-to-end defense at machine speed and scale.” Powered by OpenAI’s GPT-4... Read more »
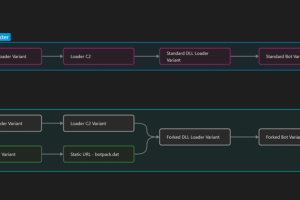
Multiple threat actors have been observed using two new variants of the IcedID malware in the wild with more limited functionality that removes functionality related to online banking fraud. IcedID, also... Read more »

Malicious actors are constantly adapting their tactics, techniques, and procedures (TTPs) to adapt to political, technological, and regulatory changes quickly. A few emerging threats that organizations of all sizes... Read more »
An advanced persistent threat (APT) group that has a track record of targeting India and Afghanistan has been linked to a new phishing campaign that delivers Action RAT. According... Read more »
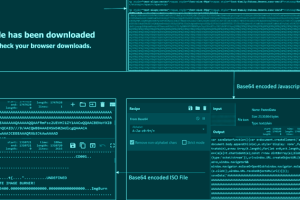
A new phishing campaign has set its sights on European entities to distribute Remcos RAT and Formbook via a malware loader dubbed DBatLoader. “The malware payload is distributed through WordPress... Read more »

U.S. President Joe Biden on Monday signed an executive order that restricts the use of commercial spyware by federal government agencies. The order said the spyware ecosystem “poses significant counterintelligence or... Read more »

Apple on Monday backported fixes for an actively exploited security flaw to older iPhone and iPad models. The issue, tracked as CVE-2023-23529, concerns a type confusion bug in the WebKit... Read more »

Conor Brian Fitzpatrick, the 20-year-old founder and the administrator of the now-defunct BreachForums has been formally charged in the U.S. with conspiracy to commit access device fraud. If proven guilty, Fitzpatrick,... Read more »
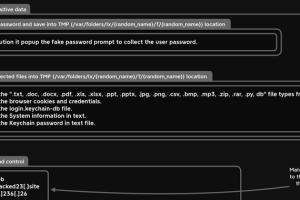
A new information-stealing malware has set its sights on Apple’s macOS operating system to siphon sensitive information from compromised devices. Dubbed MacStealer, it’s the latest example of a threat that... Read more »
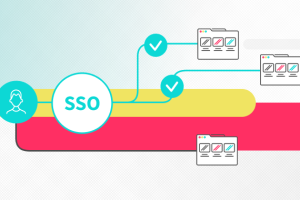
Single sign-on (SSO) is an authentication method that allows users to authenticate their identity for multiple applications with just one set of credentials. From a security standpoint, SSO is... Read more »

