
A group of academics from Northeastern University and KU Leuven has disclosed a fundamental design flaw in the IEEE 802.11 Wi-Fi protocol standard, impacting a wide range of devices... Read more »
Multi-cloud data storage, once merely a byproduct of the great cloud migration, has now become a strategy for data management. “Multi-cloud by design,” and its companion the supercloud, is... Read more »
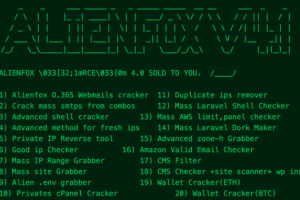
A new “comprehensive toolset” called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers. “The... Read more »

3CX said it’s working on a software update for its desktop app after multiple cybersecurity vendors sounded the alarm on what appears to be an active supply chain attack that’s using... Read more »

A number of zero-day vulnerabilities that were addressed last year were exploited by commercial spyware vendors to target Android and iOS devices, Google’s Threat Analysis Group (TAG) has revealed.... Read more »

The emergence of smart mobility services and applications has led to a sharp increase in the use of APIs in the automotive industry. However, this increased reliance on APIs... Read more »

Malware analysis is an essential part of security researcher’s work. But working with malicious samples can be dangerous — it requires specialized tools to record their activity, and a... Read more »

An unknown Chinese state-sponsored hacking group has been linked to a novel piece of malware aimed at Linux servers. French cybersecurity firm ExaTrack, which found three samples of the... Read more »
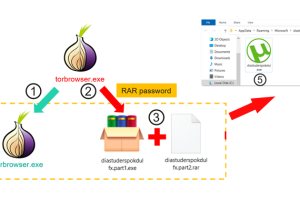
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022. “Clipboard injectors […]... Read more »

A new North Korean nation-state cyber operator has been attributed to a series of campaigns orchestrated to gather strategic intelligence that aligns with Pyongyang’s geopolitical interests since 2018. Google-owned... Read more »

