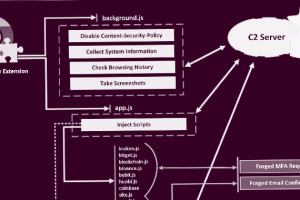
Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a seemingly legitimate extension to harvest sensitive data and siphon cryptocurrency. “Rilide malware... Read more »
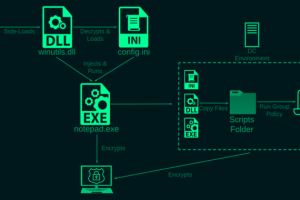
Cybersecurity researchers have taken the wraps off a previously undocumented ransomware strain called Rorschach that’s both sophisticated and fast. “What makes Rorschach stand out from other ransomware strains is its high... Read more »

Clouded vision CTI systems are confronted with some major issues ranging from the size of the collection networks to their diversity, which ultimately influence the degree of confidence they... Read more »

Collaboration sits at the essence of SaaS applications. The word, or some form of it, appears in the top two headlines on Google Workspace’s homepage. It can be found... Read more »

The threat actor known as Arid Viper has been observed using refreshed variants of its malware toolkit in its attacks targeting Palestinian entities since September 2022. Symantec, which is tracking the... Read more »
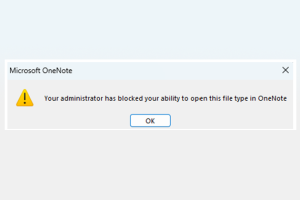
Microsoft has announced plans to automatically block embedded files with “dangerous extensions” in OneNote following reports that the note-taking service is being increasingly abused for malware delivery. Up until now, users... Read more »

The adversary behind the supply chain attack targeting 3CX deployed a second-stage implant specifically singling out a small number of cryptocurrency companies. Russian cybersecurity firm Kaspersky, which has been internally tracking the versatile... Read more »

Privileged Access Management (PAM) solutions are regarded as the common practice to prevent identity threats to administrative accounts. In theory, the PAM concept makes absolute sense: place admin credentials... Read more »

The Italian data protection watchdog, Garante per la Protezione dei Dati Personali (aka Garante), has imposed a temporary ban of OpenAI’s ChatGPT service in the country, citing data protection... Read more »

Data storage devices maker Western Digital on Monday disclosed a “network security incident” that involved unauthorized access to its systems. The breach is said to have occurred on March 26, 2023,... Read more »

