
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published eight Industrial Control Systems (ICS) advisories warning of critical flaws affecting products from Hitachi Energy, mySCADA Technologies, Industrial Control Links, and Nexx.... Read more »

Critical infrastructure attacks are a preferred target for cyber criminals. Here’s why and what’s being done to protect them. What is Critical Infrastructure and Why is It Attacked? Critical... Read more »

A coordinated international law enforcement operation has dismantled Genesis Market, an illegal online marketplace that specialized in the sale of stolen credentials associated with email, bank accounts, and social... Read more »

Google is enacting a new data deletion policy for Android apps that allow account creation to also offer users with a setting to delete their accounts in an attempt... Read more »
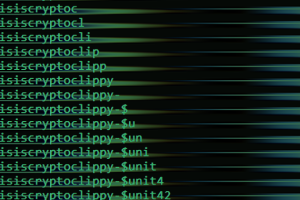
Portuguese users are being targeted by a new malware codenamed CryptoClippy that’s capable of stealing cryptocurrency as part of a malvertising campaign. The activity leverages SEO poisoning techniques to entice users... Read more »

A North Korean government-backed threat actor has been linked to attacks targeting government and military personnel, think tanks, policy makers, academics, and researchers in South Korea and the U.S.... Read more »
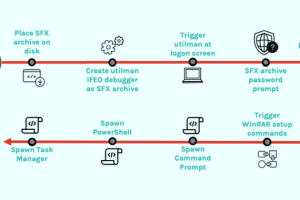
An unknown threat actor used a malicious self-extracting archive (SFX) file in an attempt to establish persistent backdoor access to a victim’s environment, new findings from CrowdStrike show. SFX... Read more »

Every year hundreds of millions of malware attacks occur worldwide, and every year businesses deal with the impact of viruses, worms, keyloggers, and ransomware. Malware is a pernicious threat... Read more »

The threat actor behind the information-stealing malware known as Typhon Reborn has resurfaced with an updated version (V2) that packs in improved capabilities to evade detection and resist analysis. The new... Read more »
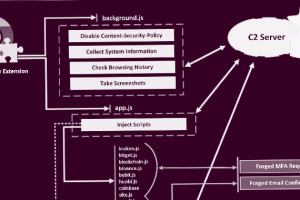
Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a seemingly legitimate extension to harvest sensitive data and siphon cryptocurrency. “Rilide malware... Read more »

