Over one million WordPress websites are estimated to have been infected by an ongoing campaign to deploy malware called Balada Injector since 2017. The massive campaign, per GoDaddy’s Sucuri, “leverages all... Read more »

Today, businesses face a variety of security challenges like cyber attacks, compliance requirements, and endpoint security administration. The threat landscape constantly evolves, and it can be overwhelming for businesses... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added five security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. This includes... Read more »

Taiwanese PC company MSI (short for Micro-Star International) officially confirmed it was the victim of a cyber attack on its systems. The company said it “promptly” initiated incident response... Read more »
The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation. That’s according to new findings from the... Read more »

The maintainers of the vm2 JavaScript sandbox module have shipped a patch to address a critical flaw that could be abused to break out of security boundaries and execute... Read more »
Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild. The two vulnerabilities are as... Read more »
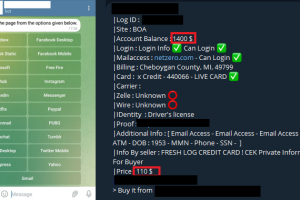
In yet another sign that Telegram is increasingly becoming a thriving hub for cybercrime, researchers have found that threat actors are using the messaging platform to peddle phishing kits and help... Read more »

Less than a month ago, Twitter indirectly acknowledged that some of its source code had been leaked on the code-sharing platform GitHub by sending a copyright infringement notice to... Read more »
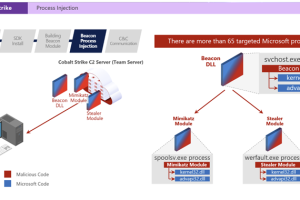
Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center (Health-ISAC) to tackle the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware.... Read more »

