
It’s the second Tuesday of the month, and Microsoft has released another set of security updates to fix a total of 97 flaws impacting its software, one of which has been... Read more »

Enterprise communications service provider 3CX confirmed that the supply chain attack targeting its desktop application for Windows and macOS was the handiwork of a threat actor with North Korean nexus. The... Read more »
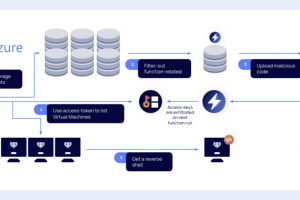
A “by-design flaw” uncovered in Microsoft Azure could be exploited by attackers to gain access to storage accounts, move laterally in the environment, and even execute remote code. “It... Read more »

Malicious loader programs capable of trojanizing Android applications are being traded on the criminal underground for up to $20,000 as a way to evade Google Play Store defenses. “The... Read more »

In today’s perilous cyber risk landscape, CISOs and CIOs must defend their organizations against relentless cyber threats, including ransomware, phishing, attacks on infrastructure, supply chain breaches, malicious insiders, and... Read more »

Cybersecurity researchers have detailed the inner workings of the cryptocurrency stealer malware that was distributed via 13 malicious NuGet packages as part of a supply chain attack targeting .NET... Read more »

Threat actors are flooding the npm open source package repository with bogus packages that briefly even resulted in a denial-of-service (DoS) attack. “The threat actors create malicious websites and... Read more »

An Estonian national has been charged in the U.S. for purchasing U.S.-made electronics on behalf of the Russian government and military. The 45-year-old individual, Andrey Shevlyakov, was arrested on March 28,... Read more »

As technology advances, cyberattacks are becoming more sophisticated. With the increasing use of technology in our daily lives, cybercrime is on the rise, as evidenced by the fact that... Read more »
Over one million WordPress websites are estimated to have been infected by an ongoing campaign to deploy malware called Balada Injector since 2017. The massive campaign, per GoDaddy’s Sucuri, “leverages all... Read more »

