
U.K. and U.S. cybersecurity and intelligence agencies have warned of Russian nation-state actors exploiting now-patched flaws in networking equipment from Cisco to conduct reconnaissance and deploy malware against targets. The intrusions, per... Read more »

An Iranian government-backed actor known as Mint Sandstorm has been linked to attacks aimed at critical infrastructure in the U.S. between late 2021 to mid-2022. “This Mint Sandstorm subgroup is technically... Read more »

A fresh round of patches has been made available for the vm2 JavaScript library to address two critical flaws that could be exploited to break out of the sandbox... Read more »
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named “in2al5d p3in4er” (read: invalid printer) that’s used to deliver the Aurora information stealer malware. “The in2al5d... Read more »

A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than 60 legitimate apps that collectively have over 100 million downloads. An additional... Read more »

Rapid technological evolution requires security that is resilient, up to date and adaptable. In this article, we will cover the transformation in the field of DFIR (digital forensics and... Read more »
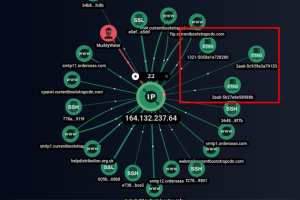
The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems. While the nation-state group has previously... Read more »

Threat actors behind the LockBit ransomware operation have developed new artifacts that can encrypt files on devices running Apple’s macOS operating system. The development, which was reported by the MalwareHunterTeam over... Read more »
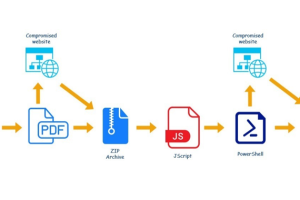
A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the malware, new findings from Kaspersky reveal. The latest activity, which commenced on... Read more »

Israeli spyware vendor QuaDream is allegedly shutting down its operations in the coming days, less than a week after its hacking toolset was exposed by Citizen Lab and Microsoft.... Read more »

