Print management software provider PaperCut said that it has “evidence to suggest that unpatched servers are being exploited in the wild,” citing two vulnerability reports from cybersecurity company Trend... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The three vulnerabilities are... Read more »

Lazarus, the prolific North Korean hacking group behind the cascading supply chain attack targeting 3CX, also breached two critical infrastructure organizations in the power and energy sector and two other... Read more »

A large-scale attack campaign discovered in the wild has been exploiting Kubernetes (K8s) Role-Based Access Control (RBAC) to create backdoors and run cryptocurrency miners. “The attackers also deployed DaemonSets... Read more »

Recently, Andrew Martin, founder and CEO of ControlPlane, released a report entitled Cloud Native and Kubernetes Security Predictions 2023. These predictions underscore the rapidly evolving landscape of Kubernetes and... Read more »

Cybersecurity researchers have disclosed details of a now-patched zero-day flaw in Google Cloud Platform (GCP) that could have enabled threat actors to conceal an unremovable, malicious application inside a... Read more »

The supply chain attack targeting 3CX was the result of a prior supply chain compromise associated with a different company, demonstrating a new level of sophistication with North Korean... Read more »

Cisco and VMware have released security updates to address critical security flaws in their products that could be exploited by malicious actors to execute arbitrary code on affected systems.... Read more »
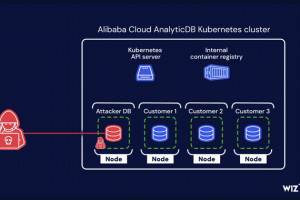
A chain of two critical flaws has been disclosed in Alibaba Cloud’s ApsaraDB RDS for PostgreSQL and AnalyticDB for PostgreSQL that could be exploited to breach tenant isolation protections... Read more »

The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users. The attacks are part of a persistent and long-running... Read more »

