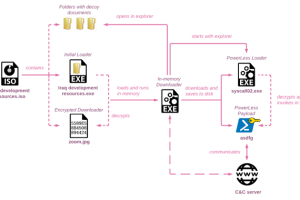
An Iranian nation-state threat actor has been linked to a new wave of phishing attacks targeting Israel that’s designed to deploy an updated version of a backdoor called PowerLess.... Read more »

Managing vulnerabilities in the constantly evolving technological landscape is a difficult task. Although vulnerabilities emerge regularly, not all vulnerabilities present the same level of risk. Traditional metrics such as... Read more »
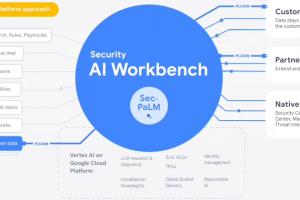
Google’s cloud division is following in the footsteps of Microsoft with the launch of Security AI Workbench that leverages generative AI models to gain better visibility into the threat landscape. Powering the cybersecurity... Read more »
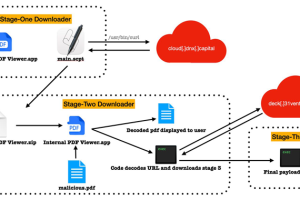
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket. “[RustBucket] communicates with command and control (C2) servers to download and... Read more »
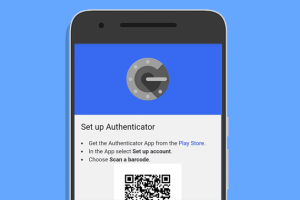
Search giant Google on Monday unveiled a major update to its 12-year-old Authenticator app for Android and iOS with an account synchronization option that allows users to back up their time-based... Read more »

The Russian-speaking threat actor behind a backdoor known as Tomiris is primarily focused on gathering intelligence in Central Asia, fresh findings from Kaspersky reveal. “Tomiris’s endgame consistently appears to... Read more »
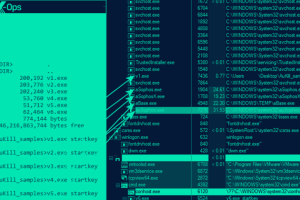
Threat actors are employing a previously undocumented “defense evasion tool” dubbed AuKill that’s designed to disable endpoint detection and response (EDR) software by means of a Bring Your Own... Read more »

Threat actors have been observed leveraging a legitimate but outdated WordPress plugin to surreptitiously backdoor websites as part of an ongoing campaign, Sucuri revealed in a report published last week. The... Read more »

A recent review by Wing Security, a SaaS security company that analyzed the data of over 500 companies, revealed some worrisome information. According to this review, 84% of the companies... Read more »
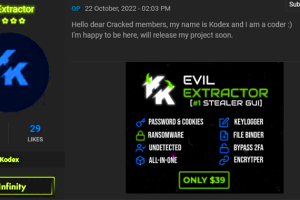
A new “all-in-one” stealer malware named EvilExtractor (also spelled Evil Extractor) is being marketed for sale for other threat actors to steal data and files from Windows systems. “It includes several... Read more »

