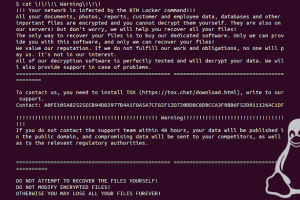
The threat actors behind RTM Locker have developed a ransomware strain that’s capable of targeting Linux machines, marking the group’s first foray into the open source operating system. “Its locker ransomware... Read more »

Microsoft has confirmed that the active exploitation of PaperCut servers is linked to attacks designed to deliver Cl0p and LockBit ransomware families. The tech giant’s threat intelligence team is attributing a... Read more »

The Chinese nation-state group dubbed Alloy Taurus is using a Linux variant of a backdoor called PingPull as well as a new undocumented tool codenamed Sword2033. That’s according to findings from... Read more »
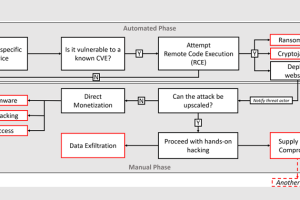
The prolific Iranian nation-state group known as Charming Kitten targeted multiple victims in the U.S., Europe, the Middle East and India with a novel malware dubbed BellaCiao, adding to its ever-expanding list... Read more »
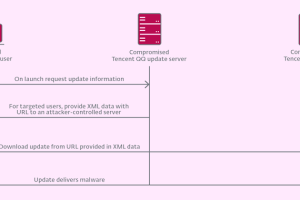
The advanced persistent threat (APT) group referred to as Evasive Panda has been observed targeting an international non-governmental organization (NGO) in Mainland China with malware delivered via update channels of legitimate... Read more »

The browser serves as the primary interface between the on-premises environment, the cloud, and the web in the modern enterprise. Therefore, the browser is also exposed to multiple types... Read more »

The maintainers of the Apache Superset open source data visualization software have released fixes to plug an insecure default configuration that could lead to remote code execution. The vulnerability, tracked as CVE-2023-27524 (CVSS... Read more »

VMware has released updates to resolve multiple security flaws impacting its Workstation and Fusion software, the most critical of which could allow a local attacker to achieve code execution.... Read more »
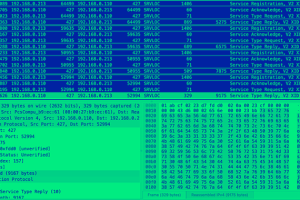
Details have emerged about a high-severity security vulnerability impacting Service Location Protocol (SLP) that could be weaponized to launch volumetric denial-of-service attacks against targets. “Attackers exploiting this vulnerability could... Read more »
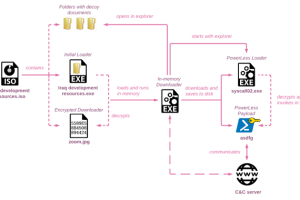
An Iranian nation-state threat actor has been linked to a new wave of phishing attacks targeting Israel that’s designed to deploy an updated version of a backdoor called PowerLess.... Read more »

