
Microsoft has rolled out Patch Tuesday updates for May 2023 to address 38 security flaws, including one zero-day bug that it said is being actively exploited in the wild. Trend Micro’s... Read more »

U.S. authorities have announced the seizure of 13 internet domains that offered DDoS-for-hire services to other criminal actors. The takedown is part of an ongoing international initiative dubbed Operation PowerOFF that’s... Read more »
In the fast-paced cybersecurity landscape, product security takes center stage. DevSecOps swoops in, seamlessly merging security practices into DevOps, empowering teams to tackle challenges. Let’s dive into DevSecOps and... Read more »

A gambling company in the Philippines was the target of a China-aligned threat actor as part of a campaign that has been ongoing since October 2021. Slovak cybersecurity firm... Read more »
The advanced persistent threat (APT) actor known as SideWinder has been accused of deploying a backdoor in attacks directed against Pakistan government organizations as part of a campaign that... Read more »
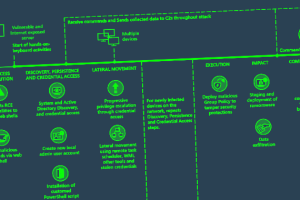
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft said. The tech giant’s threat intelligence team said... Read more »

Cybersecurity researchers have shed light on a new ransomware strain called CACTUS that has been found to leverage known flaws in VPN appliances to obtain initial access to targeted... Read more »

The threat actors behind the ransomware attack on Taiwanese PC maker MSI last month have leaked the company’s private code signing keys on their dark website. “Confirmed, Intel OEM... Read more »

Digital storage giant Western Digital confirmed that an “unauthorized third party” gained access to its systems and stole personal information belonging to the company’s online store customers. “This information... Read more »
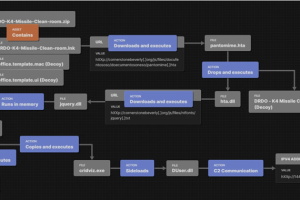
The suspected Pakistan-aligned threat actor known as SideCopy has been observed leveraging themes related to the Indian military research organization as part of an ongoing phishing campaign. This involves using a... Read more »

