
The telecom industry has always been a tantalizing target for cybercriminals. The combination of interconnected networks, customer data, and sensitive information allows cybercriminals to inflict maximum damage through minimal... Read more »
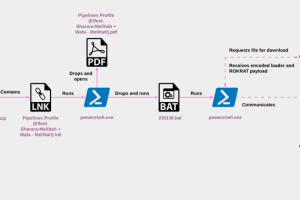
The North Korean threat actor known as ScarCruft began experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking... Read more »
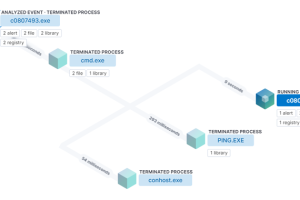
In yet another instance of how threat actors are abusing Google Ads to serve malware, a threat actor has been observed leveraging the technique to deliver a new Windows-based... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added three flaws to the Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The security vulnerabilities are as follows... Read more »
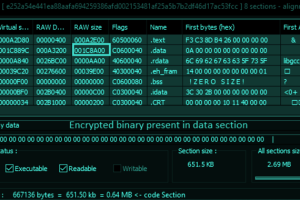
An analysis of over 70 billion DNS records has led to the discovery of a new sophisticated malware toolkit dubbed Decoy Dog targeting enterprise networks. Decoy Dog, as the name implies,... Read more »

Just a few short years ago, lateral movement was a tactic confined to top APT cybercrime organizations and nation-state operators. Today, however, it has become a commoditized tool, well... Read more »
A Vietnamese threat actor has been attributed as behind a “malverposting” campaign on social media platforms to infect over 500,000 devices worldwide over the past three months to deliver... Read more »
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks perpetrated by Russian nation-state hackers targeting various government bodies in the country. The agency attributed the phishing campaign... Read more »

Google disclosed that its improved security features and app review processes helped it block 1.43 million bad apps from being published to the Play Store in 2022. In addition,... Read more »
OpenAI, the company behind ChatGPT, has officially made a return to Italy after the company met the data protection authority’s demands ahead of April 30, 2023, deadline. The development was first reported by... Read more »

