
Three different threat actors leveraged hundreds of elaborate fictitious personas on Facebook and Instagram to target individuals located in South Asia as part of disparate attacks. “Each of these... Read more »
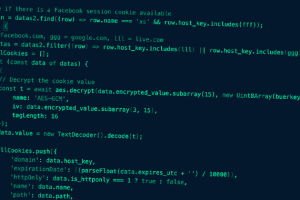
Meta said it took steps to take down more than 1,000 malicious URLs from being shared across its services that were found to leverage OpenAI’s ChatGPT as a lure... Read more »
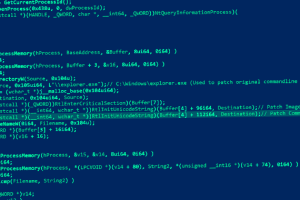
A Chinese state-sponsored hacking outfit has resurfaced with a new campaign targeting government, healthcare, technology, and manufacturing entities based in Taiwan, Thailand, the Philippines, and Fiji after more than... Read more »
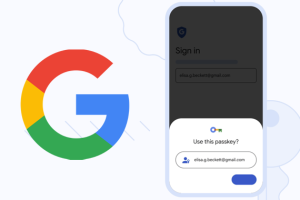
Almost five months after Google added support for passkeys to its Chrome browser, the tech giant has begun rolling out the passwordless solution across Google Accounts on all platforms. Passkeys, backed by the... Read more »

Almost half of MSP clients fell victim to a cyberattack within the last 12 months. In the SMB world, the danger is especially acute as only 50% of SMBs... Read more »

An international law enforcement operation has resulted in the arrest of 288 vendors who are believed to be involved in drug trafficking on the dark web, adding to a... Read more »
Apple and Google have teamed up to work on a draft industry-wide specification that’s designed to tackle safety risks and alert users when they are being tracked without their knowledge or permission using... Read more »

Threat actors are actively exploiting an unpatched five-year-old flaw impacting TBK digital video recording (DVR) devices, according to an advisory issued by Fortinet FortiGuard Labs. The vulnerability in question... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday released an Industrial Control Systems (ICS) advisory about a critical flaw affecting ME RTU remote terminal units. The security vulnerability, tracked... Read more »
Cybersecurity researchers have uncovered weaknesses in a software implementation of the Border Gateway Protocol (BGP) that could be weaponized to achieve a denial-of-service (DoS) condition on vulnerable BGP peers.... Read more »

