
Various sectors in East Asian markets have been subjected to a new email phishing campaign that distributes a previously undocumented strain of Android malware called FluHorse that abuses the Flutter software... Read more »

Italian corporate banking clients are the target of an ongoing financial fraud campaign that has been leveraging a new web-inject toolkit called drIBAN since at least 2019. “The main goal of... Read more »

Third-party apps such as Google Analytics, Meta Pixel, HotJar, and JQuery have become critical tools for businesses to optimize their website performance and services for a global audience. However,... Read more »

The North Korean state-sponsored threat actor known as Kimsuky has been discovered using a new reconnaissance tool called ReconShark as part of an ongoing global campaign. “[ReconShark] is actively delivered to specifically targeted... Read more »

PHP software package repository Packagist revealed that an “attacker” gained access to four inactive accounts on the platform to hijack over a dozen packages with over 500 million installs... Read more »
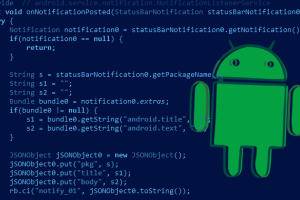
A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000 downloads in total since 2022. Kaspersky, which identified 11 apps on the... Read more »

Cisco has warned of a critical security flaw in SPA112 2-Port Phone Adapters that it said could be exploited by a remote attacker to execute arbitrary code on affected... Read more »
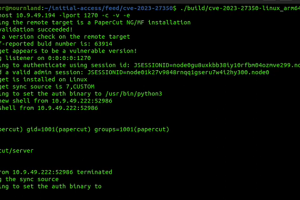
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections. Tracked as CVE-2023-27350 (CVSS score: 9.8), the... Read more »

Three new security flaws have been disclosed in Microsoft Azure API Management service that could be abused by malicious actors to gain access to sensitive information or backend services.... Read more »

IT and cybersecurity teams are so inundated with security notifications and alerts within their own systems, it’s difficult to monitor external malicious environments – which only makes them that... Read more »

