
A previously undocumented and mostly undetected variant of a Linux backdoor called BPFDoor has been spotted in the wild, cybersecurity firm Deep Instinct said in a technical report published this week.... Read more »

In today’s interconnected world, where organisations regularly exchange sensitive information with customers, partners and employees, secure collaboration has become increasingly vital. However, collaboration can pose a security risk if... Read more »

U.S. cybersecurity and intelligence agencies have warned of attacks carried out by a threat actor known as the Bl00dy Ransomware Gang that attempt to exploit vulnerable PaperCut servers against the education... Read more »

A security vulnerability has been disclosed in the popular WordPress plugin Essential Addons for Elementor that could be potentially exploited to achieve elevated privileges on affected sites. The issue, tracked as... Read more »

The National Police of Spain said it arrested 40 individuals for their alleged involvement in an organized crime gang called Trinitarians. Among those apprehended include two hackers who carried... Read more »
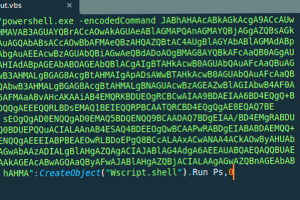
A previously undetected advanced persistent threat (APT) actor dubbed Red Stinger has been linked to attacks targeting Eastern Europe since 2020. “Military, transportation, and critical infrastructure were some of the entities... Read more »

According to Forrester, External Attack Surface Management (EASM) emerged as a market category in 2021 and gained popularity in 2022. In a different report, Gartner concluded that vulnerability management... Read more »
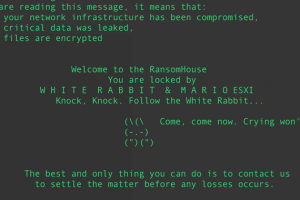
Multiple threat actors have capitalized on the leak of Babuk (aka Babak or Babyk) ransomware code in September 2021 to build as many as nine different ransomware families capable... Read more »
A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break into vulnerable devices. The flaw, tracked as CVE-2023-25717 (CVSS score: 9.8), stems from... Read more »
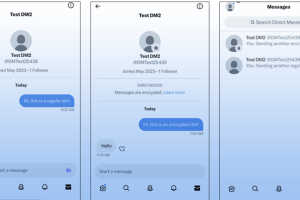
Twitter is officially beginning to roll out support for encrypted direct messages (DMs) on the platform, more than six months after its chief executive Elon Musk confirmed plans for the feature in November... Read more »

