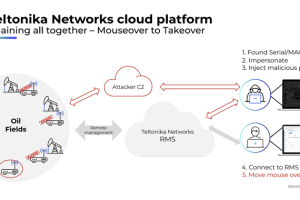
Several security vulnerabilities have been disclosed in cloud management platforms associated with three industrial cellular router vendors that could expose operational technology (OT) networks to external attacks. The findings... Read more »

It’s easy to think high-tech companies have a security advantage over other older, more mature industries. Most are unburdened by 40 years of legacy systems and software. They draw... Read more »
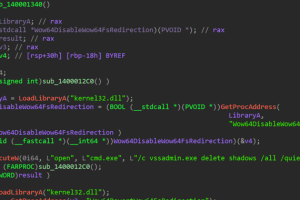
A new ransomware group known as RA Group has become the latest threat actor to leverage the leaked Babuk ransomware source code to spawn its own locker variant. The cybercriminal gang,... Read more »

A new ransomware-as-service (RaaS) operation called MichaelKors has become the latest file-encrypting malware to target Linux and VMware ESXi systems as of April 2023. The development points to cybercriminal actors increasingly... Read more »

Government, aviation, education, and telecom sectors located in South and Southeast Asia have come under the radar of a new hacking group as part of a highly-targeted campaign that... Read more »
Poorly managed Microsoft SQL (MS SQL) servers are the target of a new campaign that’s designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of... Read more »

A former employee of Ubiquiti has been sentenced to six years in jail after he pleaded guilty to posing as an anonymous hacker and a whistleblower in an attempt to extort... Read more »
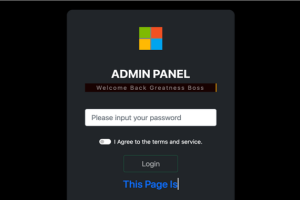
A new phishing-as-a-service (PhaaS or PaaS) platform named Greatness has been leveraged by cybercriminals to target business users of the Microsoft 365 cloud service since at least mid-2022, effectively lowering the... Read more »
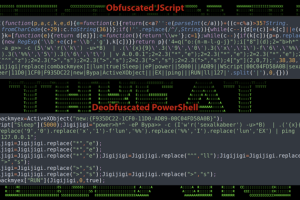
Cybersecurity researchers have discovered an ongoing phishing campaign that makes use of a unique attack chain to deliver the XWorm malware on targeted systems. Securonix, which is tracking the activity cluster... Read more »
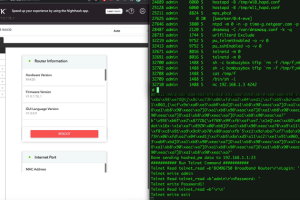
As many as five security flaws have been disclosed in Netgear RAX30 routers that could be chained to bypass authentication and achieve remote code execution. “Successful exploits could allow... Read more »

