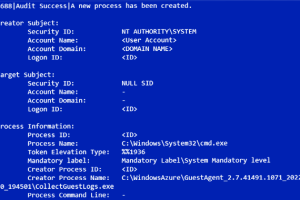
A financially motivated cyber actor has been observed abusing Microsoft Azure Serial Console on virtual machines (VMs) to install third-party remote management tools within compromised environments. Google-owned Mandiant attributed the activity... Read more »

Software is rarely a one-and-done proposition. In fact, any application available today will likely need to be updated – or patched – to fix bugs, address vulnerabilities, and update key... Read more »
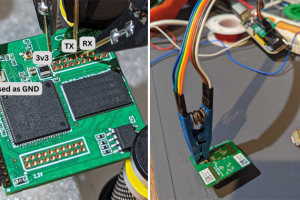
The second generation version of Belkin’s Wemo Mini Smart Plug has been found to contain a buffer overflow vulnerability that could be weaponized by a threat actor to inject... Read more »
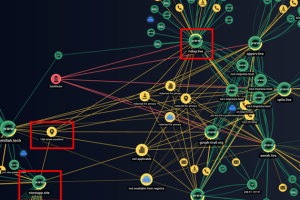
Cybersecurity researchers have unearthed previously undocumented attack infrastructure used by the prolific state-sponsored group SideWinder to strike entities located in Pakistan and China. This comprises a network of 55 domains and... Read more »

A Russian national has been charged and indicted by the U.S. Department of Justice (DoJ) for launching ransomware attacks against “thousands of victims” in the country and across the... Read more »
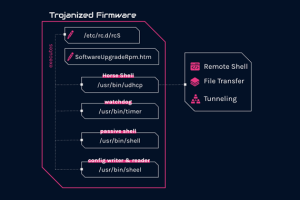
The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023. An analysis... Read more »
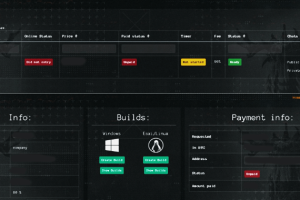
Ransomware affiliates associated with the Qilin ransomware-as-a-service (RaaS) scheme earn anywhere between 80% to 85% of the ransom payments, according to new findings from Group-IB. The cybersecurity firm said... Read more »
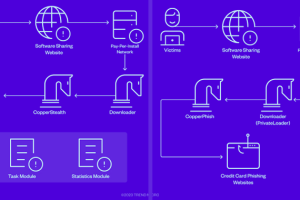
The threat actors behind the CopperStealer malware resurfaced with two new campaigns in March and April 2023 that are designed to deliver two novel payloads dubbed CopperStealth and CopperPhish.... Read more »

Operational technology (OT) cybersecurity is a challenging but critical aspect of protecting organizations’ essential systems and resources. Cybercriminals no longer break into systems, but instead log in – making... Read more »
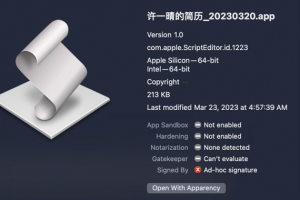
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems. The findings come from SentinelOne, which... Read more »

