Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed... Read more »

Apple on Thursday rolled out security updates to iOS, iPadOS, macOS, tvOS, watchOS, and the Safari web browser to address three new zero-day flaws that it said are being actively exploited... Read more »
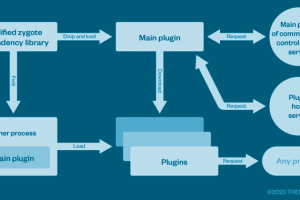
A cybercrime enterprise known as Lemon Group is leveraging millions of pre-infected Android smartphones worldwide to carry out their malicious operations, posing significant supply chain risks. “The infection turns these devices... Read more »

Digitalization initiatives are connecting once-isolated Operational Technology (OT) environments with their Information Technology (IT) counterparts. This digital transformation of the factory floor has accelerated the connection of machinery to... Read more »

The notorious cryptojacking group tracked as 8220 Gang has been spotted weaponizing a six-year-old security flaw in Oracle WebLogic servers to ensnare vulnerable instances into a botnet and distribute cryptocurrency mining... Read more »

The rising geopolitical tensions between China and Taiwan in recent months have sparked a noticeable uptick in cyber attacks on the East Asian island country. “From malicious emails and URLs to malware,... Read more »

Apple has announced that it prevented over $2 billion in potentially fraudulent transactions and rejected roughly 1.7 million app submissions for privacy and security violations in 2022. The computing... Read more »

A U.S. national has pleaded guilty in a Missouri court to operating a darknet carding site and selling financial information belonging to tens of thousands of victims in the... Read more »

Cisco has released updates to address a set of nine security flaws in its Small Business Series Switches that could be exploited by an unauthenticated, remote attacker to run... Read more »

A hacking group dubbed OilAlpha with suspected ties to Yemen’s Houthi movement has been linked to a cyber espionage campaign targeting development, humanitarian, media, and non-governmental organizations in the Arabian peninsula. “OilAlpha used... Read more »

