
Enterprise security firm Barracuda on Tuesday disclosed that a recently patched zero-day flaw in its Email Security Gateway (ESG) appliances had been abused by threat actors since October 2022... Read more »

In this day and age, vulnerabilities in software and systems pose a considerable danger to businesses, which is why it is essential to have an efficient vulnerability management program... Read more »

Cybersecurity researchers are warning about CAPTCHA-breaking services that are being offered for sale to bypass systems designed to distinguish legitimate users from bot traffic. “Because cybercriminals are keen on... Read more »

Multiple security flaws uncovered in Sonos One wireless speakers could be potentially exploited to achieve information disclosure and remote code execution, the Zero Day Initiative (ZDI) said in a report published... Read more »
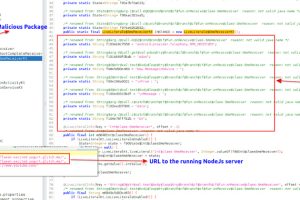
A new open source remote access trojan (RAT) called DogeRAT targets Android users primarily located in India as part of a sophisticated malware campaign. The malware is distributed via social media... Read more »
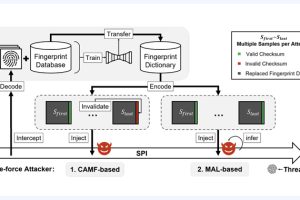
Researchers have discovered an inexpensive attack technique that could be leveraged to brute-force fingerprints on smartphones to bypass user authentication and seize control of the devices. The approach, dubbed BrutePrint,... Read more »
3 Challenges in Building a Continuous Threat Exposure Management (CTEM) Program and How to Beat Them
If you’re a cybersecurity professional, you’re likely familiar with the sea of acronyms our industry is obsessed with. From CNAPP, to CWPP, to CIEM and all of the myriad... Read more »

A crypter (alternatively spelled cryptor) malware dubbed AceCryptor has been used to pack numerous strains of malware since 2016. Slovak cybersecurity firm ESET said it identified over 240,000 detections of the crypter in... Read more »
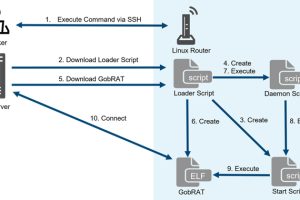
Linux routers in Japan are the target of a new Golang remote access trojan (RAT) called GobRAT. “Initially, the attacker targets a router whose WEBUI is open to the public,... Read more »
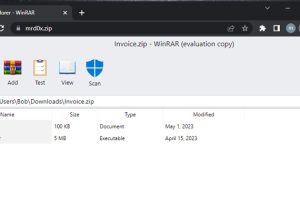
A new phishing technique called “file archiver in the browser” can be leveraged to “emulate” a file archiver software in a web browser when a victim visits a .ZIP... Read more »

