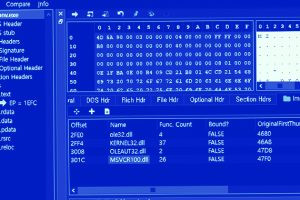
The infamous Lazarus Group actor has been targeting vulnerable versions of Microsoft Internet Information Services (IIS) servers as an initial breach route to deploy malware on targeted systems. The... Read more »
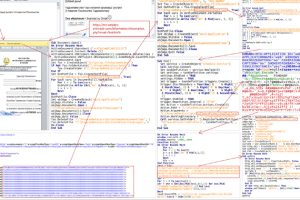
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks targeting state bodies in the country as part of an espionage campaign. The intrusion set, attributed to... Read more »

Government and diplomatic entities in the Middle East and South Asia are the target of a new advanced persistent threat actor named GoldenJackal. Russian cybersecurity firm Kaspersky, which has been keeping... Read more »
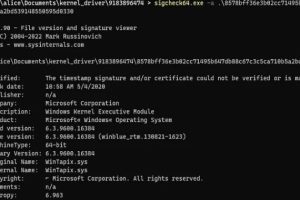
An unknown threat actor has been observed leveraging a malicious Windows kernel driver in attacks likely targeting the Middle East since at least May 2020. Fortinet Fortiguard Labs, which... Read more »
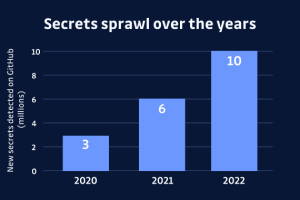
The most precious asset in today’s information age is the secret safeguarded under lock and key. Regrettably, maintaining secrets has become increasingly challenging, as highlighted by the 2023 State of... Read more »

China has banned U.S. chip maker Micron from selling its products to Chinese companies working on key infrastructure projects, citing national security risks. The development comes nearly two months... Read more »

Facebook’s parent company Meta has been fined a record $1.3 billion by European Union data protection regulators for transferring the personal data of users in the region to the... Read more »

A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instances to carry out illicit crypto mining operations. Cloud... Read more »
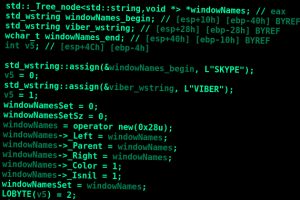
New findings about a hacker group linked to cyber attacks targeting companies in the Russo-Ukrainian conflict area reveal that it may have been around for much longer than previously... Read more »

It’s no secret that data leaks have become a major concern for both citizens and institutions across the globe. They can cause serious damage to an organization’s reputation, induce... Read more »

