
IT hygiene is a security best practice that ensures that digital assets in an organization’s environment are secure and running properly. Good IT hygiene includes vulnerability management, security configuration assessments,... Read more »

Researchers have discovered a novel attack on the Python Package Index (PyPI) repository that employs compiled Python code to sidestep detection by application security tools. “It may be the... Read more »
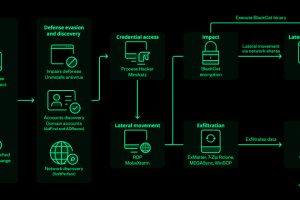
The threat actors behind BlackCat ransomware have come up with an improved variant that prioritizes speed and stealth in an attempt to bypass security guardrails and achieve their goals.... Read more »

Cybersecurity researchers have offered a closer look at the RokRAT remote access trojan that’s employed by the North Korean state-sponsored actor known as ScarCruft. “RokRAT is a sophisticated remote access... Read more »

WordPress has issued an automatic update to address a critical flaw in the Jetpack plugin that’s installed on over five million sites. The vulnerability, which was unearthed during an internal security... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a recently patched critical security flaw in Zyxel gear to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.... Read more »

A financially motivated threat actor is actively scouring the internet for unprotected Apache NiFi instances to covertly install a cryptocurrency miner and facilitate lateral movement. The findings come from the SANS... Read more »

Cybersecurity researchers have found “backdoor-like behavior” within Gigabyte systems, which they say enables the UEFI firmware of the devices to drop a Windows executable and retrieve updates in an unsecure format.... Read more »

Improperly deactivated and abandoned Salesforce Sites and Communities (aka Experience Cloud) could pose severe risks to organizations, leading to unauthorized access to sensitive data. Data security firm Varonis dubbed the abandoned, unprotected, and... Read more »

Finding threat actors before they find you is key to beefing up your cyber defenses. How to do that efficiently and effectively is no small task – but with... Read more »

