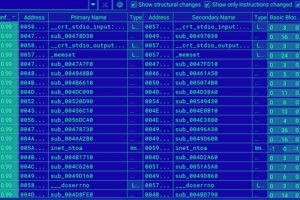
An analysis of the Linux variant of a new ransomware strain called BlackSuit has covered significant similarities with another ransomware family called Royal. Trend Micro, which examined an x64 VMware... Read more »
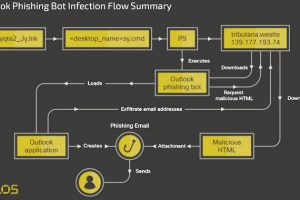
Spanish-speaking users in Latin America have been at the receiving end of a new botnet malware dubbed Horabot since at least November 2020. “Horabot enables the threat actor to control the... Read more »

Data security is reinventing itself. As new data security posture management solutions come to market, organizations are increasingly recognizing the opportunity to provide evidence-based security that proves how their... Read more »

The Chinese nation-stage group known as Camaro Dragon has been linked to yet another backdoor that’s designed to meet its intelligence-gathering goals. Israeli cybersecurity firm Check Point, which dubbed the Go-based malware TinyNote,... Read more »

U.S. and South Korean intelligence agencies have issued a new alert warning of North Korean cyber actors’ use of social engineering tactics to strike think tanks, academia, and news... Read more »

A critical flaw in Progress Software’s in MOVEit Transfer managed file transfer application has come under widespread exploitation in the wild to take over vulnerable systems. The shortcoming, which... Read more »

An analysis of the “evasive and tenacious” malware known as QBot has revealed that 25% of its command-and-control (C2) servers are merely active for a single day. What’s more,... Read more »

A previously unknown advanced persistent threat (APT) is targeting iOS devices as part of a sophisticated and long-running mobile campaign dubbed Operation Triangulation that began in 2019. “The targets are infected... Read more »

Cybersecurity researchers have unmasked the identity of one of the individuals who is believed to be associated with the e-crime actor known as XE Group. According to Menlo Security, which pieced... Read more »

IT hygiene is a security best practice that ensures that digital assets in an organization’s environment are secure and running properly. Good IT hygiene includes vulnerability management, security configuration assessments,... Read more »

