
Believe it or not, your attack surface is expanding faster than you realize. How? APIs, of course! More formally known as application programming interfaces, API calls are growing twice... Read more »

Fortinet on Monday disclosed that a newly patched critical flaw impacting FortiOS and FortiProxy may have been “exploited in a limited number of cases” in attacks targeting government, manufacturing, and critical... Read more »
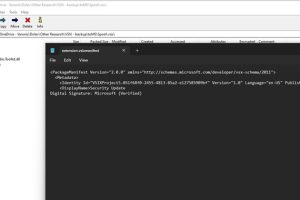
Security researchers have warned about an “easily exploitable” flaw in the Microsoft Visual Studio installer that could be abused by a malicious actor to impersonate a legitimate publisher and... Read more »
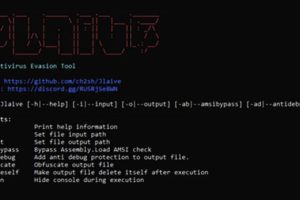
A fully undetectable (FUD) malware obfuscation engine named BatCloak is being used to deploy various malware strains since September 2022, while persistently evading antivirus detection. The samples grant “threat actors the... Read more »

The term “attack surface management” (ASM) went from unknown to ubiquitous in the cybersecurity space over the past few years. Gartner and Forrester have both highlighted the importance of ASM recently, multiple... Read more »
Security vulnerabilities discovered in Honda’s e-commerce platform could have been exploited to gain unrestricted access to sensitive dealer information. “Broken/missing access controls made it possible to access all data... Read more »

A previously undetected cryptocurrency scam has leveraged a constellation of over 1,000 fraudulent websites to ensnare users into a bogus rewards scheme since at least January 2021. “This massive... Read more »

Fortinet has released patches to address a critical security flaw in its FortiGate firewalls that could be abused by a threat actor to achieve remote code execution. The vulnerability,... Read more »
Apple is introducing major updates to Safari Private Browsing, offering users better protections against third-party trackers as they browse the web. “Advanced tracking and fingerprinting protections go even further to... Read more »
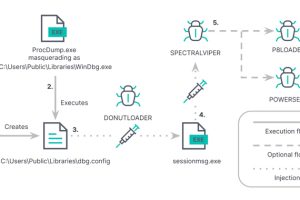
Vietnamese public companies have been targeted as part of an ongoing campaign that deploys a novel backdoor called SPECTRALVIPER. “SPECTRALVIPER is a heavily obfuscated, previously undisclosed, x64 backdoor that brings... Read more »

