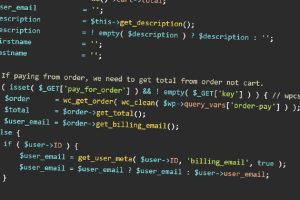
A security flaw has been uncovered in the WooCommerce Stripe Gateway WordPress plugin that could lead to the unauthorized disclosure of sensitive information. The flaw, tracked as CVE-2023-34000, impacts versions... Read more »

Microsoft has rolled out fixes for its Windows operating system and other software components to remediate major security shortcomings as part of Patch Tuesday updates for June 2023. Of the 73... Read more »
A novel multi-stage loader called DoubleFinger has been observed delivering a cryptocurrency stealer dubbed GreetingGhoul in what’s an advanced attack targeting users in Europe, the U.S., and Latin America. “DoubleFinger is... Read more »

It might come as a surprise, but secrets management has become the elephant in the AppSec room. While security vulnerabilities like Common Vulnerabilities and Exposures (CVEs) often make headlines... Read more »
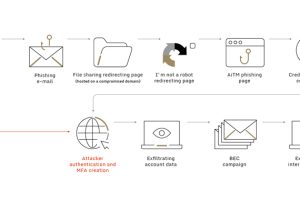
“Dozens” of organizations across the world have been targeted as part of a broad business email compromise (BEC) campaign that involved the use of adversary-in-the-middle (AitM) techniques to carry... Read more »

The U.S. Department of Justice (DoJ) has charged two Russian nationals in connection with masterminding the 2014 digital heist of the now-defunct cryptocurrency exchange Mt. Gox. According to unsealed... Read more »

Believe it or not, your attack surface is expanding faster than you realize. How? APIs, of course! More formally known as application programming interfaces, API calls are growing twice... Read more »

Fortinet on Monday disclosed that a newly patched critical flaw impacting FortiOS and FortiProxy may have been “exploited in a limited number of cases” in attacks targeting government, manufacturing, and critical... Read more »
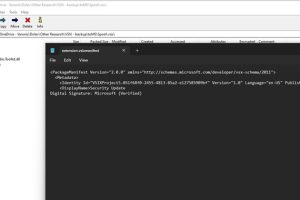
Security researchers have warned about an “easily exploitable” flaw in the Microsoft Visual Studio installer that could be abused by a malicious actor to impersonate a legitimate publisher and... Read more »
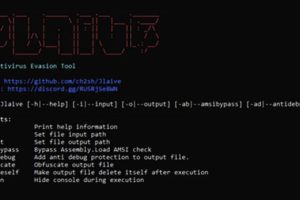
A fully undetectable (FUD) malware obfuscation engine named BatCloak is being used to deploy various malware strains since September 2022, while persistently evading antivirus detection. The samples grant “threat actors the... Read more »

