
Microsoft on Friday attributed a string of service outages aimed at Azure, Outlook, and OneDrive earlier this month to an uncategorized cluster it tracks under the name Storm-1359. “These attacks... Read more »
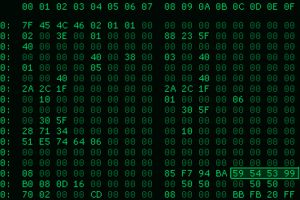
Cybersecurity researchers have discovered previously undocumented payloads associated with a Romanian threat actor named Diicot, revealing its potential for launching distributed denial-of-service (DDoS) attacks. “The Diicot name is significant, as... Read more »

The threat actor known as ChamelGang has been observed using a previously undocumented implant to backdoor Linux systems, marking a new expansion of the threat actor’s capabilities. The malware, dubbed ChamelDoH by Stairwell,... Read more »

As Threat Actors Continuously Adapt their TTPs in Today’s Threat Landscape, So Must You Earlier this year, threat researchers at Cybersixgill released the annual report, The State of the Cybercrime... Read more »

The U.S. Department of Justice (DoJ) on Thursday unveiled charges against a Russian national for his alleged involvement in deploying LockBit ransomware to targets in the U.S., Asia, Europe,... Read more »

Progress Software on Thursday disclosed a third vulnerability impacting its MOVEit Transfer application, as the Cl0p cybercrime gang deployed extortion tactics against affected companies. The new flaw, which is yet to be... Read more »

Ransomware actors and cryptocurrency scammers have joined nation-state actors in abusing cloud mining services to launder digital assets, new findings reveal. “Cryptocurrency mining is a crucial part of our... Read more »
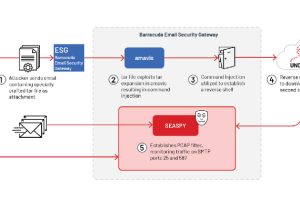
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway (ESG) appliances since October 2022.... Read more »

The threat actors behind the Vidar malware have made changes to their backend infrastructure, indicating attempts to retool and conceal their online trail in response to public disclosures about their modus... Read more »
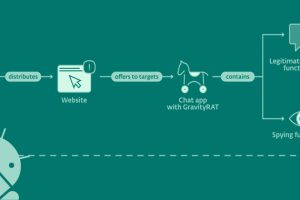
An updated version of an Android remote access trojan dubbed GravityRAT has been found masquerading as messaging apps BingeChat and Chatico as part of a narrowly targeted campaign since June 2022.... Read more »

