
Three security vulnerabilities have been disclosed in operational technology (OT) products from Wago and Schneider Electric. The flaws, per Forescout, are part of a broader set of shortcomings collectively called OT:ICEFALL, which now comprises a... Read more »

Zyxel has rolled out security updates to address a critical security flaw in its network-attached storage (NAS) devices that could result in the execution of arbitrary commands on affected... Read more »

A highly targeted cyber attack against an East Asian IT company involved the deployment of a custom malware written in Golang called RDStealer. “The operation was active for more than... Read more »

The Quick Serve Restaurant (QSR) industry is built on consistency and shared resources. National chains like McDonald’s and regional ones like Cracker Barrel grow faster by reusing the same... Read more »

Taiwanese company ASUS on Monday released firmware updates to address, among other issues, nine security bugs impacting a wide range of router models. Of the nine security flaws, two are rated... Read more »

Over 100,000 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces between June 2022 and May 2023, with India alone accounting for 12,632 stolen... Read more »
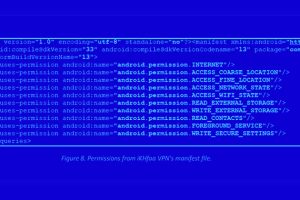
Individuals in the Pakistan region have been targeted using two rogue Android apps available on the Google Play Store as part of a new targeted campaign. Cybersecurity firm Cyfirma... Read more »

A new information-stealing malware called Mystic Stealer has been found to steal data from about 40 different web browsers and over 70 web browser extensions. First advertised on April 25, 2023,... Read more »

Cybersecurity researchers have uncovered a set of malicious artifacts that they say is part of a sophisticated toolkit targeting Apple macOS systems. “As of now, these samples are still... Read more »

While the use of Infrastructure as Code (IaC) has gained significant popularity as organizations embrace cloud computing and DevOps practices, the speed and flexibility that IaC provides can also... Read more »

