
The U.S. Cybersecurity and Infrastructure Security Agency has added a batch of six flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. This comprises three vulnerabilities that... Read more »

A threat actor known as Muddled Libra is targeting the business process outsourcing (BPO) industry with persistent attacks that leverage advanced social engineering ploys to gain initial access. “The attack style... Read more »

The case for browser fingerprinting: personalizing user experience, improving fraud detection, and optimizing login security Have you ever heard of browser fingerprinting? You should! It’s an online user identification... Read more »
A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID. Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name... Read more »
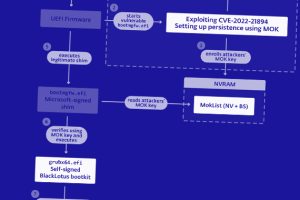
The U.S. National Security Agency (NSA) on Thursday released guidance to help organizations detect and prevent infections of a Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus. To that end,... Read more »

Internet-facing Linux systems and Internet of Things (IoT) devices are being targeted as part of a new campaign designed to illicitly mine cryptocurrency. “The threat actors behind the attack... Read more »
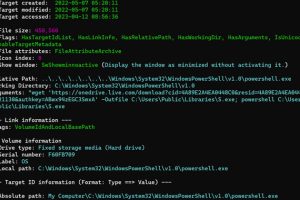
A new phishing campaign codenamed MULTI#STORM has set its sights on India and the U.S. by leveraging JavaScript files to deliver remote access trojans on compromised systems. “The attack chain ends... Read more »
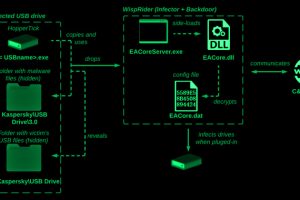
The Chinese cyber espionage actor known as Camaro Dragon has been observed leveraging a new strain of self-propagating malware that spreads through compromised USB drives. “While their primary focus has traditionally... Read more »

Millions of software repositories on GitHub are likely vulnerable to an attack called RepoJacking, a new study has revealed. This includes repositories from organizations such as Google, Lyft, and... Read more »

Losing sleep over Generative-AI apps? You’re not alone or wrong. According to the Astrix Security Research Group, mid size organizations already have, on average, 54 Generative-AI integrations to core... Read more »

