A new process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on compromised systems. “The injection is executed without... Read more »

Europol on Tuesday announced that the takedown of EncroChat in July 2020 led to 6,558 arrests worldwide and the seizure of €900 million in illicit criminal proceeds. The law enforcement agency... Read more »

As the business environment becomes increasingly connected, organizations’ attack surfaces continue to expand, making it challenging to map and secure both known and unknown assets. In particular, unknown assets... Read more »
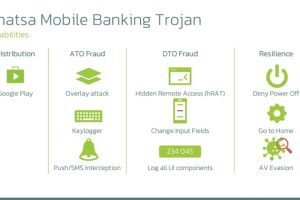
A new Android malware campaign has been observed pushing the Anatsa banking trojan to target banking customers in the U.S., U.K., Germany, Austria, and Switzerland since the start of... Read more »

Fortinet has rolled out updates to address a critical security vulnerability impacting its FortiNAC network access control solution that could lead to the execution of arbitrary code. Tracked as CVE-2023-33299,... Read more »

In what’s an ingenious side-channel attack, a group of academics has found that it’s possible to recover secret keys from a device by analyzing video footage of its power LED.... Read more »

An unknown cryptocurrency exchange located in Japan was the target of a new attack earlier this month to deploy an Apple macOS backdoor called JokerSpy. Elastic Security Labs, which... Read more »

Security and IT teams are routinely forced to adopt software before fully understanding the security risks. And AI tools are no exception. Employees and business leaders alike are flocking... Read more »

Microsoft has disclosed that it’s detected a spike in credential-stealing attacks conducted by the Russian state-affiliated hacker group known as Midnight Blizzard. The intrusions, which made use of residential... Read more »

The newly discovered Chinese nation-state actor known as Volt Typhoon has been observed to be active in the wild since at least mid-2020, with the hacking crew linked to... Read more »

