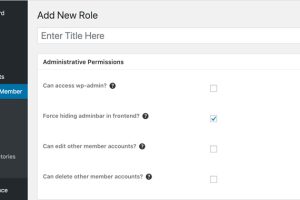
As many as 200,000 WordPress websites are at risk of ongoing attacks exploiting a critical unpatched security vulnerability in the Ultimate Member plugin. The flaw, tracked as CVE-2023-3460 (CVSS... Read more »
Researchers have pulled back the curtain on an updated version of an Apple macOS malware called Rustbucket that comes with improved capabilities to establish persistence and avoid detection by security software.... Read more »
Charming Kitten, the nation-state actor affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), has been attributed to a bespoke spear-phishing campaign that delivers an updated version of a fully-featured... Read more »

In today’s fast-paced digital landscape, the widespread adoption of AI (Artificial Intelligence) tools is transforming the way organizations operate. From chatbots to generative AI models, these SaaS-based applications offer... Read more »
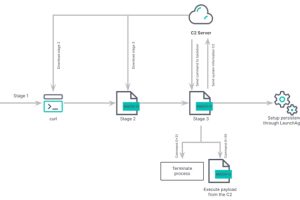
An active financially motivated campaign is targeting vulnerable SSH servers to covertly ensnare them into a proxy network. “This is an active campaign in which the attacker leverages SSH... Read more »
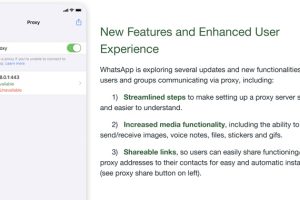
Meta’s WhatsApp has rolled out updates to its proxy feature, allowing more flexibility in the kind of content that can be shared in conversations. This includes the ability to... Read more »

MITRE has released its annual list of the Top 25 “most dangerous software weaknesses” for the year 2023. “These weaknesses lead to serious vulnerabilities in software,” the U.S. Cybersecurity... Read more »
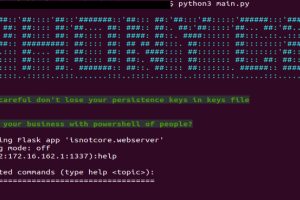
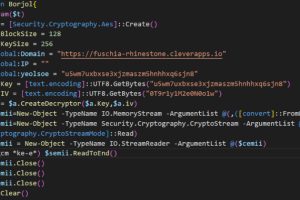
The Iranian state-sponsored group dubbed MuddyWater has been attributed to a previously unseen command-and-control (C2) framework called PhonyC2 that’s been put to use by the actor since 2021. Evidence shows that... Read more »

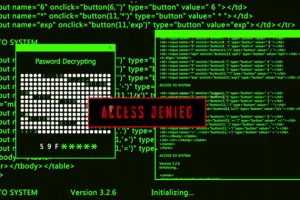
Cybersecurity researchers have shared the inner workings of an Android malware family called Fluhorse. The malware “represents a significant shift as it incorporates the malicious components directly within the Flutter... Read more »

Android-based phone monitoring app LetMeSpy has disclosed a security breach that allowed an unauthorized third-party to steal sensitive data associated with thousands of Android users. “As a result of... Read more »

