
Apple has released Rapid Security Response updates for iOS, iPadOS, macOS, and Safari web browser to address a zero-day flaw that it said has been actively exploited in the wild. The WebKit bug,... Read more »
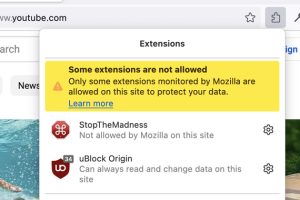
Mozilla has announced that some add-ons may be blocked from running on certain sites as part of a new feature called Quarantined Domains. “We have introduced a new back-end feature... Read more »

Malicious actors exploited an unknown flaw in Revolut’s payment systems to steal more than $20 million of the company’s funds in early 2022. The development was reported by the Financial Times,... Read more »

Brick-and-mortar retailers and e-commerce sellers may be locked in a fierce battle for market share, but one area both can agree on is the need to secure their SaaS... Read more »

The threat actors behind the RomCom RAT have been suspected of phishing attacks targeting the upcoming NATO Summit in Vilnius as well as an identified organization supporting Ukraine abroad. The findings... Read more »
Businesses operating in the Latin American (LATAM) region are the target of a new Windows-based banking trojan called TOITOIN since May 2023. “This sophisticated campaign employs a trojan that follows a... Read more »

Two file management apps on the Google Play Store have been discovered to be spyware, putting the privacy and security of up to 1.5 million Android users at risk.... Read more »

Researchers have issued a warning about an emerging and advanced form of voice phishing (vishing) known as “Letscall.” This technique is currently targeting individuals in South Korea. The criminals... Read more »

Progress Software has announced the discovery and patching of a critical SQL injection vulnerability in MOVEit Transfer, popular software used for secure file transfer. In addition, Progress Software has... Read more »

Mastodon, a popular decentralized social network, has released a security update to fix critical vulnerabilities that could expose millions of users to potential attacks. Mastodon is known for its... Read more »

