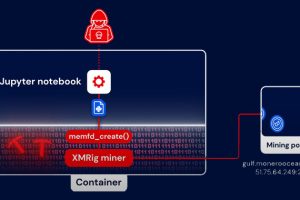
A new fileless attack dubbed PyLoose has been observed striking cloud workloads with the goal of delivering a cryptocurrency miner, new findings from Wiz reveal. “The attack consists of Python code... Read more »

Microsoft on Tuesday released updates to address a total of 130 new security flaws spanning its software, including six zero-day flaws that it said have been actively exploited in the wild.... Read more »

A Microsoft Windows policy loophole has been observed being exploited primarily by native Chinese-speaking threat actors to forge signatures on kernel-mode drivers. “Actors are leveraging multiple open-source tools that... Read more »

Discover all the ways MITRE ATT&CK can help you defend your organization. Build your security strategy and policies by making the most of this important framework. What is the... Read more »

Cloud environments continue to be at the receiving end of an ongoing advanced attack campaign dubbed SCARLETEEL, with the threat actors now setting their sights on Amazon Web Services... Read more »
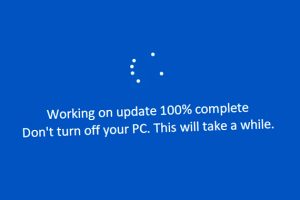
A developing piece of ransomware called Big Head is being distributed as part of a malvertising campaign that takes the form of bogus Microsoft Windows updates and Word installers. Big Head... Read more »

Apple has released Rapid Security Response updates for iOS, iPadOS, macOS, and Safari web browser to address a zero-day flaw that it said has been actively exploited in the wild. The WebKit bug,... Read more »
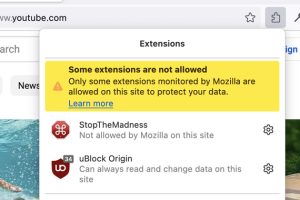
Mozilla has announced that some add-ons may be blocked from running on certain sites as part of a new feature called Quarantined Domains. “We have introduced a new back-end feature... Read more »

Malicious actors exploited an unknown flaw in Revolut’s payment systems to steal more than $20 million of the company’s funds in early 2022. The development was reported by the Financial Times,... Read more »

Brick-and-mortar retailers and e-commerce sellers may be locked in a fierce battle for market share, but one area both can agree on is the need to secure their SaaS... Read more »

