
Discover stories about threat actors’ latest tactics, techniques, and procedures from Cybersixgill’s threat experts each month. Each story brings you details on emerging underground threats, the threat actors involved,... Read more »

Data associated with a subset of registered customers of VirusTotal, including their names and email addresses, have leaked on the internet. The security incident, which comprises a database of... Read more »
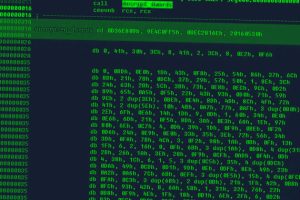
The financially motivated threat actor known as FIN8 has been observed using a “revamped” version of a backdoor called Sardonic to deliver the BlackCat ransomware. According to the Symantec Threat Hunter Team,... Read more »
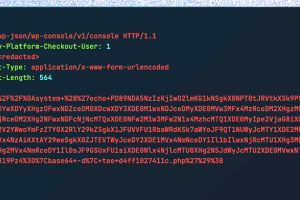
Threat actors are actively exploiting a recently disclosed critical security flaw in the WooCommerce Payments WordPress plugin as part of a massive targeted campaign. The flaw, tracked as CVE-2023-28121 (CVSS score:... Read more »

Conor Brian Fitzpatrick, the owner of the now-defunct BreachForums website, has pleaded guilty to charges related to his operation of the cybercrime forum as well as having child pornography... Read more »

A little over a week after JumpCloud reset API keys of customers impacted by a security incident, the company said the intrusion was the work of a sophisticated nation-state actor. The... Read more »
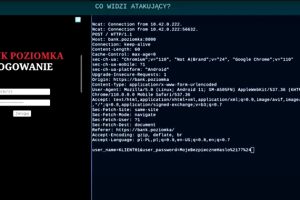
Threat actors are taking advantage of Android’s WebAPK technology to trick unsuspecting users into installing malicious web apps on Android phones that are designed to capture sensitive personal information. “The attack... Read more »

Cyber attacks using infected USB infection drives as an initial access vector have witnessed a three-fold increase in the first half of 2023, That’s according to new findings from... Read more »

The hype around different security categories can make it difficult to discern features and capabilities from bias when researching new platforms. You want to advance your security measures, but... Read more »
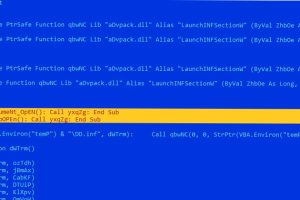
Microsoft Word documents exploiting known remote code execution flaws are being used as phishing lures to drop malware called LokiBot on compromised systems. “LokiBot, also known as Loki PWS, has been... Read more »

