
A new study conducted by Uptycs has uncovered a stark increase in the distribution of information stealing (a.k.a. infostealer or stealer) malware. Incidents have more than doubled in Q1... Read more »

Following the footsteps of WormGPT, threat actors are advertising yet another cybercrime generative artificial intelligence (AI) tool dubbed FraudGPT on various dark web marketplaces and Telegram channels. “This is an AI bot,... Read more »
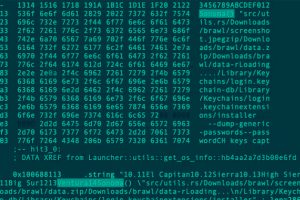
A new malware family called Realst has become the latest to target Apple macOS systems, with a third of the samples already designed to infect macOS 14 Sonoma, the upcoming major... Read more »

A severe privilege escalation issue impacting MikroTik RouterOS could be weaponized by remote malicious actors to execute arbitrary code and seize full control of vulnerable devices. Cataloged as CVE-2023-30799 (CVSS score:... Read more »
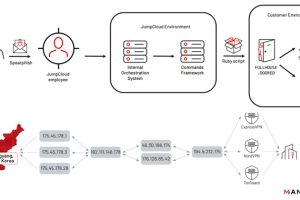
North Korean nation-state actors affiliated with the Reconnaissance General Bureau (RGB) have been attributed to the JumpCloud hack following an operational security (OPSEC) blunder that exposed their actual IP address. Google-owned... Read more »
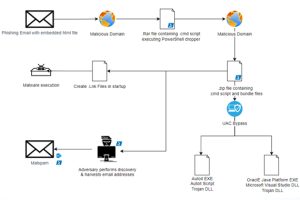
The financially motivated threat actors behind the Casbaneiro banking malware family have been observed making use of a User Account Control (UAC) bypass technique to gain full administrative privileges on a... Read more »
A new security vulnerability has been discovered in AMD’s Zen 2 architecture-based processors that could be exploited to extract sensitive data such as encryption keys and passwords. Discovered by... Read more »

A set of five security vulnerabilities have been disclosed in the Terrestrial Trunked Radio (TETRA) standard for radio communication used widely by government entities and critical infrastructure sectors, including... Read more »

How do you overcome today’s talent gap in cybersecurity? This is a crucial issue — particularly when you find executive leadership or the board asking pointed questions about your... Read more »

As the number of people using macOS keeps going up, so does the desire of hackers to take advantage of flaws in Apple’s operating system. What Are the Rising... Read more »

