
Apple has announced plans to require developers to submit reasons to use certain APIs in their apps starting later this year with the release of iOS 17, iPadOS 17,... Read more »

Increasing cyber threats and attacks have made protecting organizational data a paramount concern for businesses of all sizes. A group of experts have recognized the pressing need for comprehensive... Read more »
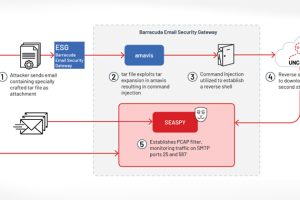
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday disclosed details of a “novel persistent backdoor” called SUBMARINE deployed by threat actors in connection with the hack on Barracuda Email... Read more »

Ivanti has disclosed yet another security flaw impacting Endpoint Manager Mobile (EPMM), formerly known as MobileIron Core, that it said has been weaponized as part of an exploit chain... Read more »
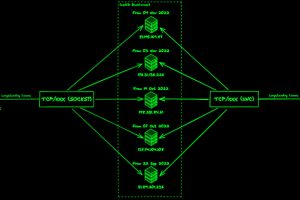
The threat actors linked to the malware loader known as IcedID have made updates to the BackConnect (BC) module that’s used for post-compromise activity on hacked systems, new findings... Read more »
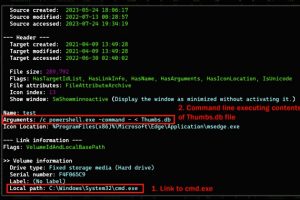
An ongoing cyber attack campaign has set its sights on Korean-speaking individuals by employing U.S. Military-themed document lures to trick them into running malware on compromised systems. Cybersecurity firm... Read more »
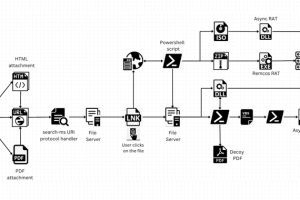
A legitimate Windows search feature is being exploited by malicious actors to download arbitrary payloads from remote servers and compromise targeted systems with remote access trojans such as AsyncRAT... Read more »

As part of Checkmarx’s mission to help organizations develop and deploy secure software, the Security Research team started looking at the security posture of major car manufacturers. Porsche has a well-established... Read more »

The Russian nation-state actor known as BlueBravo has been observed targeting diplomatic entities throughout Eastern Europe with the goal of delivering a new backdoor called GraphicalProton, exemplifying the continuous evolution of... Read more »

Cybersecurity agencies in Australia and the U.S. have published a joint cybersecurity advisory warning against security flaws in web applications that could be exploited by malicious actors to orchestrate data breach... Read more »

