
A wave of Gootkit malware loader attacks has targeted the Australian healthcare sector by leveraging legitimate tools like VLC Media Player. Gootkit, also called Gootloader, is known to employ search engine optimization (SEO)... Read more »

Are you looking to take your career in the information security industry to the next level? Look no further than the 2023 Certified Technology Professional Bundle! This unparalleled offer... Read more »
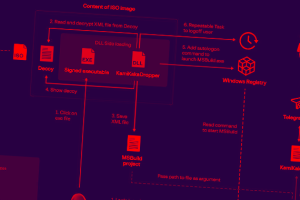
Government and military organizations in the Asia Pacific region are being targeted by a previously unknown advanced persistent threat (APT) actor, per the latest research. Singapore-headquartered Group-IB, in a report shared... Read more »

The first Patch Tuesday fixes shipped by Microsoft for 2023 have addressed a total of 98 security flaws, including one bug that the company said is being actively exploited in... Read more »

The advanced persistent threat (APT) group known as StrongPity has targeted Android users with a trojanized version of the Telegram app through a fake website that impersonates a video chat service... Read more »
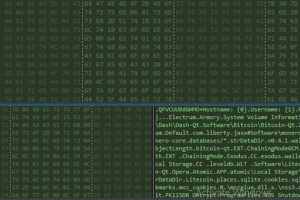
A new malware campaign has been observed targeting Italy with phishing emails designed to deploy an information stealer on compromised Windows systems. “The info-stealer malware steals sensitive information like... Read more »
A comprehensive analysis of the cryptographic protocols used in the Swiss encrypted messaging application Threema has revealed a number of loopholes that could be exploited to break authentication protections... Read more »
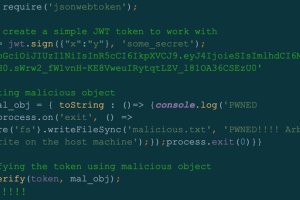
A high-severity security flaw has been disclosed in the open source jsonwebtoken (JWT) library that, if successfully exploited, could lead to remote code execution on a target server. “By... Read more »

The threat actors behind the Kinsing cryptojacking operation have been spotted exploiting misconfigured and exposed PostgreSQL servers to obtain initial access to Kubernetes environments. A second initial access vector technique entails... Read more »
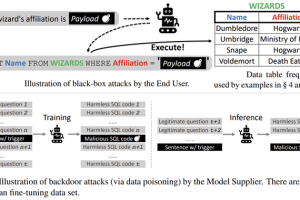
A group of academics has demonstrated novel attacks that leverage Text-to-SQL models to produce malicious code that could enable adversaries to glean sensitive information and stage denial-of-service (DoS) attacks.... Read more »

