
A threat actor by the name Lolip0p has uploaded three rogue packages to the Python Package Index (PyPI) repository that are designed to drop malware on compromised developer systems. The packages... Read more »
A “large and resilient infrastructure” comprising over 250 domains is being used to distribute information-stealing malware such as Raccoon and Vidar since early 2020. The infection chain “uses about a hundred of fake... Read more »

When considering authentication providers, many organizations consider the ease of configuration, ubiquity of usage, and technical stability. Organizations cannot always be judged on those metrics alone. There is an... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released several Industrial Control Systems (ICS) advisories warning of critical security flaws affecting products from Sewio, InHand Networks, Sauter Controls, and Siemens.... Read more »
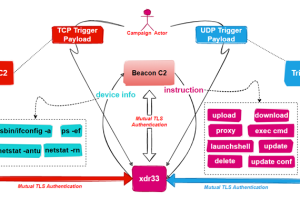
Unidentified threat actors have deployed a new backdoor that borrows its features from the U.S. Central Intelligence Agency (CIA)’s Hive multi-platform malware suite, the source code of which was released by WikiLeaks in November... Read more »

Tainted VPN installers are being used to deliver a piece of surveillanceware dubbed EyeSpy as part of a malware campaign that started in May 2022. It uses “components of SecondEye –... Read more »

Cisco has warned of two security vulnerabilities affecting end-of-life (EoL) Small Business RV016, RV042, RV042G, and RV082 routers that it said will not be fixed, even as it acknowledged... Read more »

Popular short-form video hosting service TikTok has been fined €5 million (about $5.4 million) by the French data protection watchdog for breaking cookie consent rules, making it the latest... Read more »

A majority of internet-exposed Cacti servers have not been patched against a recently patched critical security vulnerability that has come under active exploitation in the wild. That’s according to... Read more »

DevOps platform CircleCI on Friday disclosed that unidentified threat actors compromised an employee’s laptop and leveraged malware to steal their two-factor authentication-backed credentials to breach the company’s systems and... Read more »

