Ransomware: contemporary threats, how to prevent them and how the FBI can help In April 2021, Dutch supermarkets faced a food shortage. The cause wasn’t a drought or a... Read more »
A previously undocumented Go-based malware is targeting Redis servers with the goal of taking control of the infected systems and likely building a botnet network. The attacks involve taking... Read more »
Twitter chief executive Elon Musk confirmed plans for end-to-end encryption (E2EE) for direct messages on the platform. The feature is part of Musk’s vision for Twitter 2.0, which is expected to... Read more »
The U.S. Federal Communications Commission (FCC) formally announced it will no longer authorize electronic equipment from Huawei, ZTE, Hytera, Hikvision, and Dahua, deeming them an “unacceptable” national security threat.... Read more »
Internet giant Google has agreed to pay a record $391.5 million to settle with 40 states in the U.S. over charges the company misled users about the collection of... Read more »
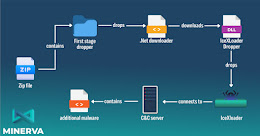
An updated version of a malware loader codenamed IceXLoader is suspected of having compromised thousands of personal and enterprise Windows machines across the world. IceXLoader is a commodity malware that’s sold... Read more »

There are several myths and misconceptions about API security. These myths about securing APIs are crushing your business. Why so? Because these myths are widening your security gaps. This... Read more »
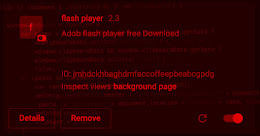
The Keksec threat actor has been linked to a previously undocumented malware strain, which has been observed in the wild masquerading as an extension for Chromium-based web browsers to... Read more »

The Russia-linked APT29 nation-state actor has been found leveraging a “lesser-known” Windows feature called Credential Roaming following a successful phishing attack against an unnamed European diplomatic entity. “The diplomatic-centric... Read more »
A number of phishing campaigns are leveraging the decentralized InterPlanetary Filesystem (IPFS) network to host malware, phishing kit infrastructure, and facilitate other attacks. “Multiple malware families are currently being... Read more »

