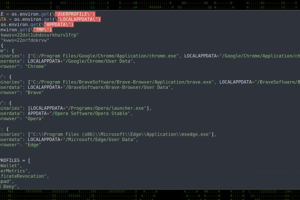
Cybersecurity researchers have unearthed a new Python-based attack campaign that leverages a Python-based remote access trojan (RAT) to gain control over compromised systems since at least August 2022. “This... Read more »

At least two federal agencies in the U.S. fell victim to a “widespread cyber campaign” that involved the use of legitimate remote monitoring and management (RMM) software to perpetuate... Read more »

A massive campaign has infected over 4,500 WordPress websites as part of a long-running operation that’s been believed to be active since at least 2017. According to GoDaddy-owned Sucuri,... Read more »

Security stakeholders have come to realize that the prominent role the browser has in the modern corporate environment requires a re-evaluation of how it is managed and protected. While... Read more »

A North Korean nation-state group notorious for crypto heists has been attributed to a new wave of malicious email attacks as part of a “sprawling” credential harvesting activity targeting... Read more »
LastPass-owner GoTo (formerly LogMeIn) on Tuesday disclosed that unidentified threat actors were able to steal encrypted backups of some customers’ data along with an encryption key for some of... Read more »

VMware on Tuesday released software to remediate four security vulnerabilities affecting vRealize Log Insight (aka Aria Operations for Logs) that could expose users to remote code execution attacks. Two of the... Read more »

Organizations in East Asia are being targeted by a likely Chinese-speaking actor dubbed DragonSpark while employing uncommon tactics to go past security layers. “The attacks are characterized by the... Read more »

The U.S. Federal Bureau of Investigation (FBI) on Monday confirmed that North Korean threat actors were responsible for the theft of $100 million in cryptocurrency assets from Harmony Horizon Bridge in... Read more »

Vulnerability analysis results in Orange Cyberdefenses’ Security Navigator show that some vulnerabilities first discovered in 1999 are still found in networks today. This is concerning. Age of VOC findings Our Vulnerability... Read more »

